Our clients


.svg.png?width=1200&height=389&name=1200px-Capita_logo_(2019).svg.png)
.png?width=800&height=362&name=FIFA_series_logo.svg%20(1).png)



.png?width=590&height=205&name=BNP%20Paribas%20Logo%20(1).png)
A comprehensive, evidence-based assessment
A mature, cyber-resilient organisation can be defined as a business that can continue to operate, service its clients, deliver a public service, satisfy its shareholders and continue to make a profit, despite being under a cyber-attack. An effective, responsive and resilient organisation is always alert and on the look-out for early signs of malicious activity and pounces on the slightest of suspicious events with the intention of nipping them in the bud.
This comprehensive, no-holds barred assessment, provides a 360-degree view of your organisation’s cyber incident response and crisis readiness. We don’t just interview stakeholders, we scrutinise each and every in-scope artefact and insist on supporting evidence for each item.
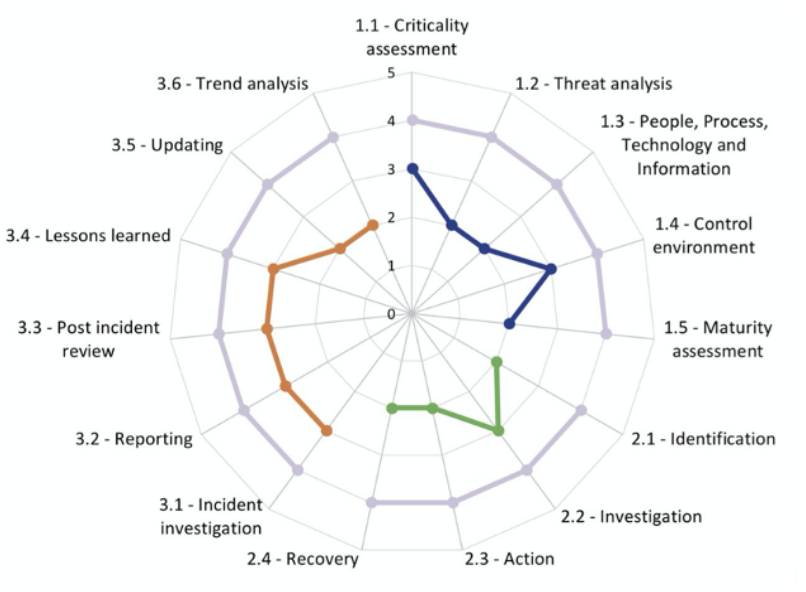
The Cyber Resilience Maturity Assessment is one of our most comprehensive, evidence-based assessments and it comes with an executive summary and detailed ‘improvements’ report. This audit also evaluates the SIEM and other technology stack implementation and the organisation’s SOC operations.
Summarised, a resilient business can:
- Rapidly detect and respond to an incident.
- Quickly and accurately identify, investigate and classify an incident.
- Safely recover from an attack and securely resume business operations.
- Capture, analyse and process data from the attack to create, share and maintain attack knowledge.
- Resume business operations with zero to little disruption.

Benefits
- Obtain a comprehensive, 360-view of your organisation’s cyber-resilience maturity measured against easy-to-understand NIST-based Incident Handling categories.
- Understand how your approach to incident response aligns with NIST's approach to incident response.
- Understand how your approach to incident response aligns with ISO 27001:2013’s Annex A.16.1, Incident Management Lifecycle.
- Gain a deep understanding of your detection, response and recovery capabilities across the breadth and depth of your organisation’s operations and strategy.
- Identify upgrade opportunities across a cross-section of your organisation’s pillars of people, processes and technology.
- Identify improvements in operational workflows in the Security Operations.
- Significant opportunity to improve the whole organisation’s cyber resilience posture.
What We Examine
During our comprehensive Cyber Incident Response Maturity Assessment, we:
- Review documentation sets including policies, processes, procedures and technological standards.
- Review monitoring coverage, configured alerts, processes, use-cases and use-case-responses.
- Interview key stakeholders including senior management, management and technical resources.
- Will attempt to understand your monitoring landscape, SIEM and related detection and response technology.
- Review incident lifecycle management approach, processes and procedures.
- Review incident handling process, SOC team structure and skillset.
- Evaluate inter-departmental cooperation in incident handling.
- Review incident handling timelines against the defined processes.
.jpg)
Stakeholders
One of the main objectives of this exercise is to collate and understand what the expected outcome of the service is. To this end, we seek to speak to stakeholders including, but not limited to:
- Project sponsors.
- Executives including CISO, IT Director, IT Security
- Change/Service Management
- GRC team/risk team
- Head of Security Operations, Security Engineering, Forensics
- Third-party and supply chain involved in supporting the security service
- Security analysts operating the SIEM
- Threat management team, network security, AD team, Windows/Systems team
Approach
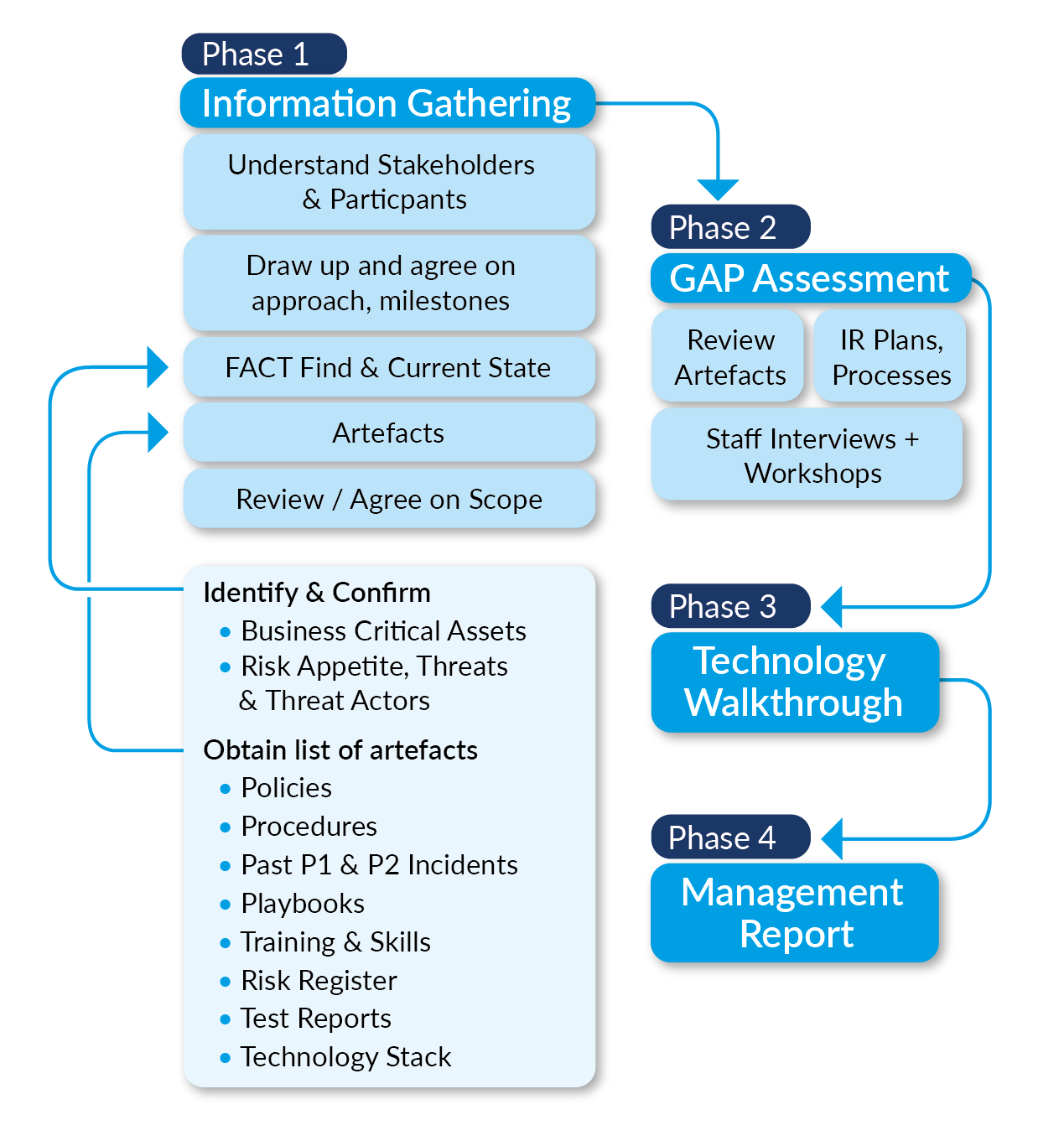
We adopt the same rigour, discipline and evidence-based approach to all our assessments. In Phase 1, we are in a ‘fact-finding’ mode and want to read and consume all the necessary information. Although we speak to staff in Phase 1, we tend to have more meaningful discussions in Phase 2, as we are more informed and hence more prepared with the right questions.
For the technology assessments, we prefer technology walkthroughs so we can get a feel of the setup, mode of use and configurations. We also get a feel of what a ‘day’ looks like for the operator of the technology.
We then complete the assignment with a management report.
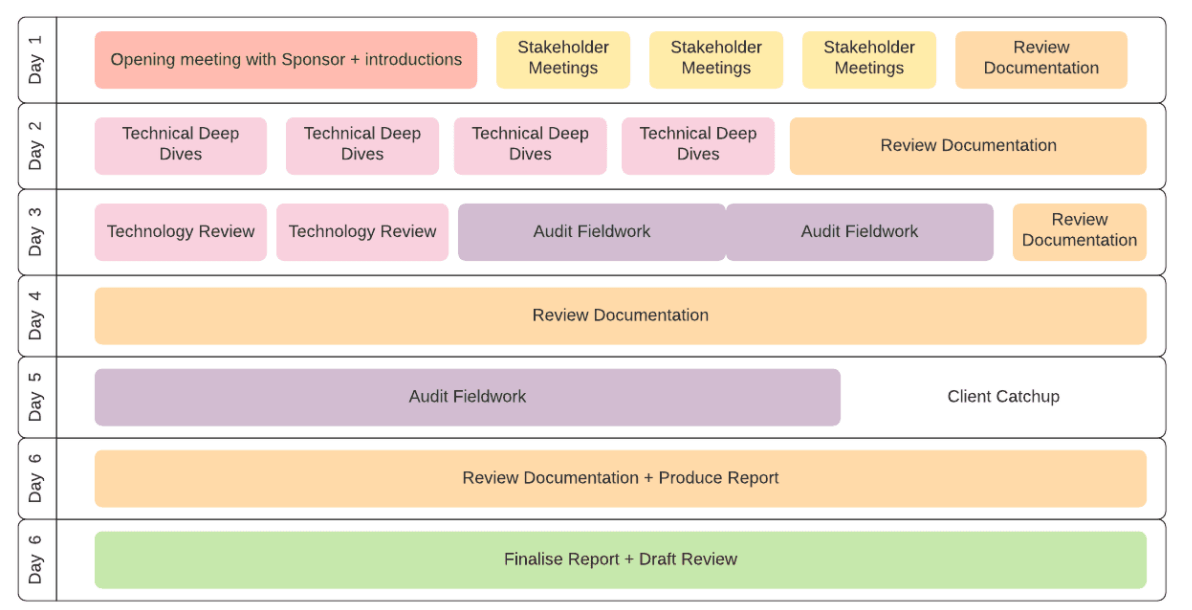
Sample Assessment Schedule
Please note this is an approximation and the actual effort may vary depending on the client, the size of the SOC, the number of analysts and other factors.
3 Key Benefits of Conducting a Cyber Incident Maturity Assessment
360-View
Obtain a comprehensive, 360-view of your organisation’s cyber-resilience maturity measured against easy-to-understand NIST-based categories.
Understanding
Gain a deep understanding of your detection, response and recovery capabilities across the breadth and depth of your organisation’s operations and strategy.
Identify
Client Testimonials
We have assisted numerous organisations including FIFA, NHS, Capita, BNP Paribas, Formula One Racing, British Medical Journal, and many more with assessments and audits. Here's some feedback from just a few of them.

Mudassar Ulhaq - Chief Information Officer -Waverton Investment Management
"I would recommend Cyber Management Alliance’s tabletop workshops to anyone genuinely interested in being on top of their cyber incident response strategies. The format and style of conducting the entire workshop is what I found a lot of value in. Most importantly, the scenarios on which the workshop was based were relevant to the business, making the exercise a great investment of time and resources."

Aaron Townsend - Service Delivery Manager - British Medical Journal
"In order for BMJ to the right way forward we looked for a VCISO to advise us on the right way to do things and give us expertise. We went to Cyber Management Alliance and it's been about a year now and we ran workshops, looked at our response to incidents, created the incident response plan and we are in a position now where we understand our way forward. Our VCISO keeps us on our toes and overall it's been a very effective way of delivering expertise into the organisation that we wouldn't have normally had."

Neil Mallon - Strategic Technology Leader - Aster Housing
"The Cyber Crisis Tabletop Exercise and corresponding audit conducted by Cyber Management Alliance Ltd was expertly delivered and has given us insights to reinforce our cyber strategy by continuing to help build the picture of where we were, where we are now, and our next focussed steps. We will be engaging CM-Alliance on an annual basis."
Why not book a discovery call to discuss your requirements?
Why not find out more about our audits and assessments? Book a no-obligation discovery call with one of our consultants.
We provide support on cybersecurity strategy, policies, incident response, gap assessments, SIEM assessments, GDPR, Cyber Crisis Tabletop Exercises, Breach Readiness Assessments, and more. Speak to us to find out how we can assist.
James C - CEO, UK Hedge Fund
Amar and the team at Cyber Management Alliance have been a huge help in getting our firm positioned to deal with cyber security risk. Having opened our eyes to the variety and scale of challenges we face, and the potential financial consequences, they worked closely with us to improve our infrastructure, processes and understanding to embed cyber awareness into the firm. Their invaluable experience has guided us to the point where we should receive ISO27001 accreditation in the coming weeks – a key stamp of approval that lets clients know we take these risks very seriously.

