Technical Cyber-Attack Tabletop Exercises
A Cyber Attack Tabletop Exercise for Technical Staff validates your technical team's ability to handle and respond to a real cyber-attack. The IT Crisis Simulation deep dives into your technical abilities and the individual skills of team members to successfully mitigate the damage that a cybersecurity incident can cause.
Why are structured IT Cyber Drills so critical to your business?
Technical teams sit on the frontline of cybersecurity defences. The increasing complexity and number of cyber-attacks necessitates practical, engaging, and comprehensive training methods. Our Cyber Attack Tabletop Exercises for technical and IT staff are structured scenarios that help technical staff anticipate, identify, and respond to cyber threats in a controlled, risk-free environment. These exercises are pivotal in bridging the gap between theoretical knowledge and real-world cyber attack readiness.
What Actually Happens during a Technical Incident Response Exercise?
During the actual technical Incident Response exercise, all participants are put under pressure to think and act like they would in the event of a real world cybersecurity attack. Through the discussions that take place, the facilitator evaluates the skills and knowledge of each team member with respect to the Incident Response plans and processes of the organisation. In the Technical Cyber Security Drill, specifically, the technical knowledge as well as the participants' familiarity with the technical controls and technology tools becomes apparent.
Find out more about our different categories of Cyber Tabletop Exercises and Cyber Tabletop Exercise Pricing
The Target Audience
A tabletop exercise is only as good as the participants. The ideal audience for a Technical Cyber-Attack Tabletop Exercise is listed below:
- Systems Architects
- Network Specialists
- Windows/Linux specialists
- Cloud Infra Specialists
- SoC/Security analysts
- IT Security engineers
- Data Base Administrators
- Technical/Configuration specialist
- Product owners
- Change Management Expert
Common Challenges that Technical Cyber Drills Address
Technical Cyber Tabletop Exercises are crucial for testing and improving your organisation’s incident response capabilities. Businesses often face significant challenges in bringing together technical and non-technical teams for a unified response to cyber threats. Below are key obstacles that technical cyber drills can address:
Siloed Technical Teams
Overconfidence in Technical Tools
Overreliance on technical tools can lead to delayed threat detection and misinterpretation, weakening response efforts. Cyber drills help technical teams assess the true effectiveness of these tools and uncover blind spots or areas that need human intervention.
Overlooked Dependencies & Risks
Many organisations have single points of failure like key personnel with exclusive system access. Overlooked supply chain risks such as third-party vendors with insecure APIs are another frequent concern. Technical cyber drills expose these vulnerabilities effectively, encouraging technical teams to build proactive detection and response strategies.
Outdated Threat Scenarios
The technical team may often overlook the most current and emerging cyber threat scenarios. Technical Cyber Drills focus on novel attack vectors such as AI-driven phishing attacks and zero-day exploits. They help technical teams adapt to evolving tactics of threat actors such as ransomware with data exfiltration or double extortion.
Regulatory Non-Compliance
It is not uncommon for technical teams to lose sight of larger business requirements such as regulatory compliance. Technical Cyber Drills ensure compliance with cybersecurity regulations (PCI DSS, GDPR, DORA etc.), improve documentation, and provide an audit trail of preparedness efforts.
Cultural Resistance
Technical teams often resist simulated cyber attack drills due to fear of blame, skepticism, or reluctance to interrupt daily tasks for 'hypothetical' incident preparation. However, drills conducted by cybersecurity experts can uncover significant blind spots and demonstrate the value that these exercises bring to IT and technical teams.
Benefits of Conducting a Technical Cyber Tabletop Exercise
A professionally conducted technical cyber drill has numerous benefits and related outcomes for both the organisation and the tabletop participants.
Some of these include:
- Builds 'muscle memory' and better recall of critical actions and processes.
- Creates a long lasting 'top of the mind' recall.
- Facilitates and increases inter-departmental collaboration.
- Helps discover technical and process gaps without conducting expensive pen-tests.
- Builds better confidence of all team members.
- Enables demonstrating and meeting regulatory compliance (where applicable).
Validates Technical Breach Readiness
As the name suggests, a technical tabletop exercises tests and validates the effectiveness of your existing tools and technical controls. Most importantly, it helps your technical teams and analysts to respond effectively and efficiently to a cyber-attack. It bolsters overall IT incident management.
Improves the Team's Technical Skills
The most important element in an organisation's cybersecurity posture is the human element. The Cyber Attack Simulation exercise is one of the most accurate ways to improve the technical competencies of your Incident Responders and enhance technical team's cyber incident readiness.
An Inexpensive Expert Pentest
A Technical Tabletop Exercise takes a close & hard look at your technology infrastructure. We deep dive into the existing technology and processes and dig for gaps and loopholes that most urgently need to be plugged. Essentially, it's almost like a Penetration Test minus the exorbitant costs.
Dynamic & Evolving Scenarios
Working with the client we create detailed Cyber Attack Workflows. The workflow is implemented along with a dynamic and evolving attack scenario which is made all the more realistic through injects over time. This keeps the technical staff motivated & makes the exercise a true test of your IT team's mettle.
Creates Technical Confidence
The biggest benefit of a Technical Tabletop Exercise is that it leads to peace of mind and confidence in the technical team. The management of the organisation can rest easy knowing that the technical team has been trained and tested in responding effectively to a cyber-attack.
Helps Achieve Regulatory Compliance
For businesses in specific countries & industries, it is mandatory to demonstrate the efficacy of technical controls in dealing with a cyber attack. A Technical Cyber Crisis Drill helps you achieve compliance with any such regulatory requirement applicable to your business.
What Makes Our Technical Cyber Attack Tabletop Exercises Uniquely Effective?
Our Technical Cyber Security Drills are a great way to validate your organisation's technical capability to handle a cyber-attack. Our unique and detail-oriented approach to technical tabletop exercises means they come as close as possible to a Penetration Test without actually being one - that's also what makes them cost-effective.
Here is why our technical cyber drills are unique and effective:
- You get to conduct an intense scrutiny of your technical and technological apparatus at a fraction of the cost.
- We use our extensive experience in pen-testing to ensure we have the most viable attack scenario with realistic cyber attack vectors. This keeps the technical staff engaged and helps sharpen their knowledge for better technical response coordination.
- With a focus on future cyber-attack readiness, these exercises keep IT and technical staff motivated towards the importance of their specific roles in maintaining the cybersecurity posture of the business.
Here are some specific features of the Technical Cyber Tabletop Drill conducted by Cyber Management Alliance that makes them stand out in the market:
Relentless Attention to Detail
Unlike a generic Cyber Tabletop Exercise, a Technical Tabletop Exercise requires deep analytical and technical skills during the planning stage as it is geared specifically towards a technical audience.
We spend a lot of time working on the technical attack scenario and related questions to ensure relevancy.
Our goal is to challenge the technical Incident Responders.
Focus on Technical Response
We leverage detailed Cyber Attack Workflows during the Technical Tabletop Workshop.
This makes the exercise intense and productive with a razor-sharp focus on the actual 'response'. We delve deep into what technical response they elicit at each stage.
This helps the team build insight and muscle memory for when the business is under an actual attack and damage needs to be controlled in real time.
Highly Experienced Facilitators
Our Technical Cyber Attack Tabletop Exercises are facilitated by deeply experienced practitioners.
They have been deep in the trenches themselves through their work in technical & Incident Response teams across multiple organisations.
The attack scenario, the questions asked and the discussions facilitated could not be more real and thought provoking.
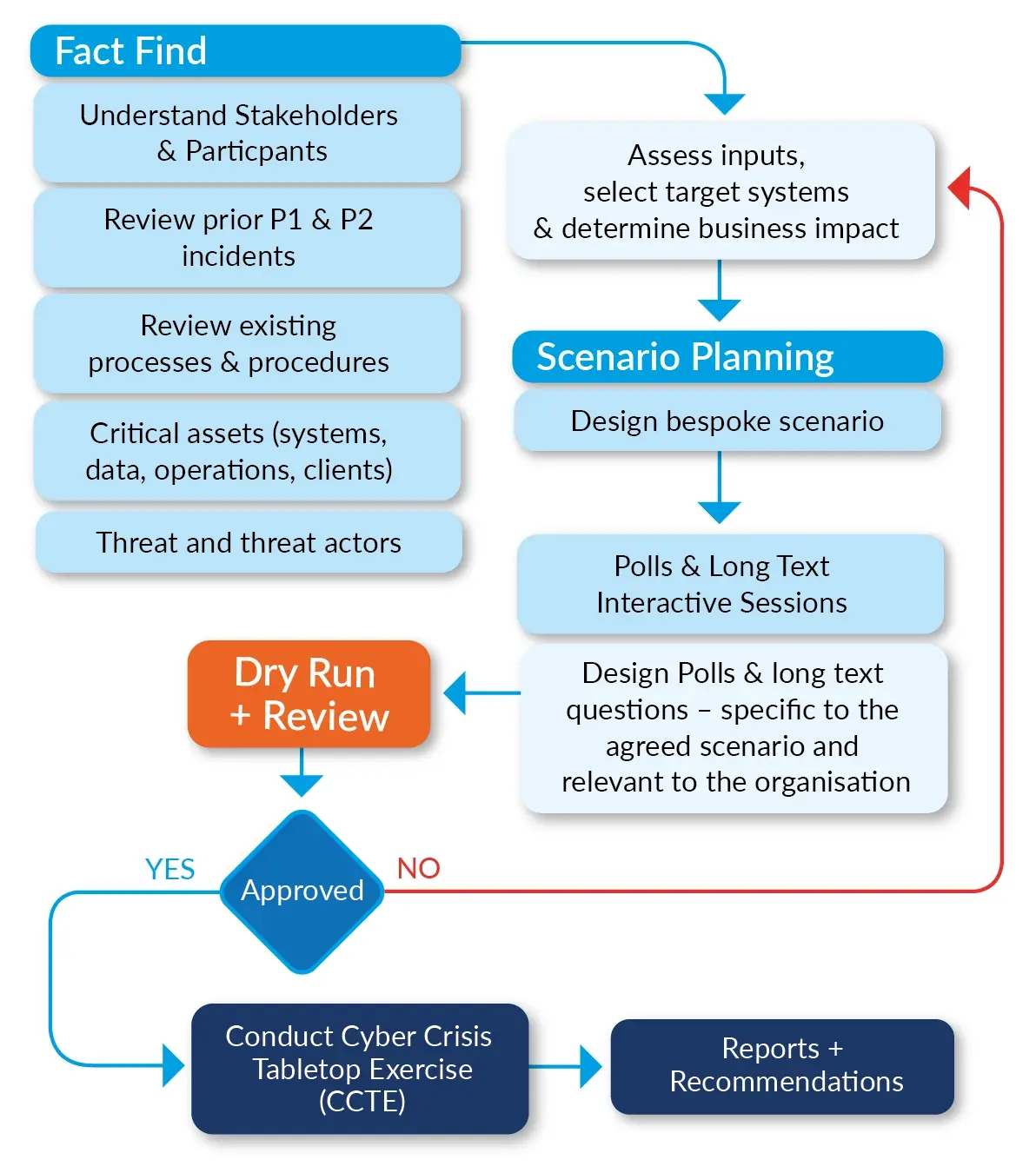
Planning for a Technical Cyber Drill
The planning stage of the scenario for the IT staff cyber readiness session is critical. It involves deep work between our expert facilitator and one or more representatives from the Client's side. During this stage, the cybersecurity expert explores and exhausts all possible attack scenarios on the critical assets of the organisation. The primary points of discussion at this stage are:
- Tools, technology and security solutions employed by the organisation.
- Intense scrutiny of gaps in the technology controls
- Careful examination of the organisational Incident Response and related processes.
The discussions and deliberations in the planning stage are then converted into the actual technical scenario for the Cyber Attack Simulation Exercise.
Case Studies demonstrate how others have benefited from our Tabletop Exercises. We have numerous client case studies which demonstrate how these sessions have helped clients optimise their handling of cyber incidents. Click the button below to check out some of our Case Studies.
Delivery: Meticulously Curated Professionally Designed Session

First Impressions Count
We take great care in producing the content for the technical cyber tabletop session. Each image, each technical detail is meticulously selected to ensure maximum relevancy and participation.
Interaction: Designed & Delivered to ensure Maximum Participation

Participation is Everything
A cyber drill is lifeless without audience interaction. We design each question and facilitate each session with one aim in mind - enabling maximum audience interaction & keeping technical staff engaged.
Deeply Engaging & Interactive Cyber Drills for Technical Staff
You can have the best content but a lifeless delivery loses the audience very quickly. Consequently, an uninterested and bored team means the objectives and outcomes are unachievable.
We ensure lively and engaging delivery by ensuring:
- Only a professional experienced facilitator conducts the session.
- Produced content is reviewed and approved by the Client with one or more dry runs.
The video on the right gives an insight into how we engage and interact, and help you get the best value out of your Tabletop Exercises.
Read our Clients' Experience with the Technical Cyber Tabletop Exercise
"Both the technical and executive tabletop sessions conducted by Cyber Management Alliance Ltd met all our objectives. The attendees from both the sessions were impressed with the facilitation and the outcome-driven approach and left the participants more informed and aware of the response processes and procedures.”
Nadeem Bashir
IT Compliance Manager, Otsuka Pharmaceutical Europe Ltd.
FAQs: Technical Cyber Drills
Can we conduct a cyber drill ourselves?
You absolutely can and should conduct regular tabletop or cyber drill exercises. However, our existing clients tell us of significant increases in interactivity and audience engagement after they hired us as external tabletop facilitators. There are several benefits of hiring an unbiased, external expert who can offer a valuable outsider's experienced perspective.
Why should we use the CM-Alliance interactive platform?
The use of our interactive platform during a cyber drill ensures maximum participation. For example, if 12 people have joined a tabletop session, we can ensure that we have 12 responses to each question presented to the participants.
Additionally, as the responses are formally captured:
- We aggregate and map the answers and present them in our NIST-friendly report (Detect, Analyse, Contain, Eradicate, Respond and Recover).
- The Client can structure any training and improvement plans and align the training and outputs to NIST and other standards.
Can we anonymise the answers to the questions?
Yes. We do not show the names of the respondents during the actual tabletop session. The names are only revealed after the exercise is complete. We DO NOT list the names of the respondents against the answers in the final report.
How long does planning take?
It's not easy to provide a binary number to this question. A lot depends on the complications of the asset, complexity of the infrastructure and how 'spread' the asset is (in terms of geography etc.).
Why do you insist on detailed planning?
Conducting a technical cyber drill is fairly easy.
Conducting a meaningful, interactive and engaging cyber tabletop exercise for technical staff, however, requires sufficient planning, attention to detail and professional facilitation.
Anyone can put up a PowerPoint or an animated slide. Very few can engage the various attendees from the IT and technical teams to ensure relevancy and maximum participation.
Is this a memory test of how many processes I can recall?
Nope. Although we are not going to penalise you for perfect memory and recall. That's an amazing skill to have.
However, what we are looking for is the recall of of critical processes, the awareness of IR protocols, the ability to create high level actions (in the absence of any) and more.
What are Hybrid Sessions and why should we avoid them?
Hybrid sessions are a mix of onsite and virtual sessions where a group of people is physically present in one location and several others are connected via MS Teams or Zoom.
We DO NOT recommend hybrid sessions (where some are remote and some are onsite) as they severely degrade the overall video and audio performance.
Should we conduct a cyber drill remotely or onsite?
All other variables being equal, we recommend a remote session as, anecdotally, a majority of incidents happen during unearthly hours and a remote or virtual cyber drill helps simulate a real life incident.
We DO NOT recommend hybrid sessions (where some are remote and some are onsite).
How long does a technical cyber drill exercise last for?
Our shortest technical cyber tabletop exercise has been for 90 minutes (The client was a very small organisation). Most technical sessions last between 2 -3 hours. We have had exceptionally long technical tabletop sessions too - a total of 2 full days!
What are the absolute bare minimums for a successful tech tabletop session?
We could write several pages but here are the 'absolute bare minimums' we look for from the Client side:
- Critical Asset: The Client must select the correct and MOST critical asset for the technical tabletop session. There's no point selecting a video conferencing asset as the 'target' asset if it's not a business critical asset.
- BIA or Business Impact Analysis: Related to the above, it really helps the technical cyber mock drill if the client has conducted their BIA. If not, we can help conduct one.
- Frank and Honest Discussion: We need all the information during our planning stage (and yes, we do sign NDAs with clients). We are unable to conduct a full and contextual tabletop exercise if the client does not share all the information about its assets and infrastructure.
- Visuals: Sounds trivial but as they say - a picture can speak a thousand words! A network visual and/or a visual of 'how it all fits together' is very helpful in constructing a tangible and fit-for-purpose cyber drill.
Trusted by

.webp?width=800&height=362&name=FIFA_series_logo.svg%20(1).webp)



Why not book a discovery call to discuss your requirements?
Want more information on our Technical Cyber Tabletop Exercises? Book a no-obligation discovery call with one of our consultants.
All trademarks, service marks, trade names, product names, service names and logos appearing on the site, or on printed or digital material are the property of their respective owners, including in Cyber Management Alliance Ltd. Any rights not expressly granted herein are reserved. The information on this page and related pages and documents is Copyright of Cyber Management Alliance Ltd. The VCC or Virtual Cyber Consultant term, other terms, information, concepts, ideas, workflows, processes, procedures and other content that directly or indirectly supports the VCC Service are Copyright of Cyber Management Alliance Ltd. Copyright 2023



