What is a Virtual Cyber Assistant?
The Virtual Cyber Assistant Service is a globally-accessible, subscription-based, cyber-consultancy-as-a-service. We cater to all types of businesses, regardless of where they are located. We adopt an asynchronous approach to providing our service which nullifies the impact of working in different time zones.
Why hire a Virtual Cyber Assistant?
There is a massive dearth of highly-skilled cybersecurity practitioners across the globe. Further, it's expensive and often complicated to recruit, employ and retain professionals from this small pool of specialized individuals. Our Virtual Cyber Assistant or VCA Service aims to plug this gap for all types and sizes of businesses globally.
You have tried to hire experienced cybersecurity professionals but you either couldn't find the right fit or the right kind of talent was too expensive.
Your require on-demand support to demonstrate cybersecurity maturity to meet Regulatory or Contractual requirements.
You would like to seriously enhance your cybersecurity posture and improve maturity over a specific time-period that works for your business.
You want to bolster cyber resilience & have your cybersecurity artefacts professionally reviewed in a cost and time-effective way.
What Makes Our Virtual Cyber Assistant Service Unique?
The Virtual Cyber Assistant Model is affordable and specially tailored for the large number of micro & small businesses that cannot afford exorbitant consultancy fees to achieve their cyber security goals & stay prepared for the increasing number of cyber-attacks.
Multiple Subscription Tiers
We have created 4 Service Tiers to match your cybersecurity requirements - Silver, Gold, Platinum, and Platinum+. Whether you need something done gradually or have an urgent requirement for achieving certification, we have a Service Tier for you.
Flexible Payment Plans
Clients can choose to pay monthly (pay-as-you-go) or annually. When you subscribe to the monthly plan, there is no commitment. Annual clients, who pay upfront for 12 months or more, are entitled to a discount of up to 30% on the monthly charge. In addition, annual paying clients have access to many additional benefits and premium features including extra Zoom hours.
Access to 280+ cyber services
Our VCA service follows a unique, asynchronous approach to delivering world-class cybersecurity services. Our clients get easy access to 280+ Cybersecurity, Governance, Risk & Compliance Services across 15 Domains. We also offer readymade packages including Cyber Essentials, ISO 27001, BCP & more.
Duties & Tasks Your Virtual Assistant Can Perform For You
| If you need to demonstrate cybersecurity control maturity to clients. |
| If you need to fill in a cybersecurity questionnaire for a client. |
| If you do not have any Cybersecurity framework and/or want to make sure you follow best practices. |
| If your customers are asking you to become Cyber Essentials Certified and you need comprehensive support in this area. |
| If your internal team has filled in the Cyber Essentials questionnaire but you need an external review before final submission. |
| If your management is worried about the lack of standards and/or cyber frameworks in the organisation. Therefore, you want to align the business with the ISO 27001:2022 Standard. |
| If you do not have any Cyber Risk Management Framework and you want to follow best practices. |
| If you need Incident Response Playbooks created, reviewed and/or refreshed. |
| If you need a complete review of your Business Continuity & Disaster Recovery plans. |
| If you've just conduced a pen-test and need a professional to review and opine on the report. You may also need someone to create a corrective action plan. |
| If you have to present a report on the maturity of cybersecurity controls to the management. |
| If you need assistance in selecting the best technological DR solution. |
| If you are not prepared to respond to and recover from cyber-attacks and ransomware attacks and need support in creating and implementing a cybersecurity incident response plan along with related processes and response playbooks. |
| If, due to an increasing number of suppliers, you need to review cybersecurity practices in Supply Chain and define processes in accordance with the best practices. |
| If you do not have any defined processes to manage cybersecurity in the supply chain. |
| If you do not necessarily want to be certified with ISO 27001 but want only the Risk Management Framework implemented. |
| If you understand that the first step towards Risk Management is identifying assets and their classification. You want help to identify assets and define asset management processes. |
| If you need to review cybersecurity practices in Asset Management and define processes in accordance with the best practices. |
| If your customer wants you to submit one or more documents detailing your cybersecurity best practices and you do not have anything in place currently. |
| If someone asked about your cybersecurity maturity and you now feel the need to better understand and evaluate your maturity levels. |
| If you have no cyber strategy to guide your organisation for this year and the next and you need to create a cybersecurity strategy for your organisation. |
What differentiates our Virtual Cyber Assistant Service from other consultancies?
Asynchronous, Ticket-Only Service: Our focus and emphasis, with the VCA Service, is to offer an asynchronous, ticket-only based approach. This means we can service clients globally at a budget that is palatable to a large number of businesses. The asynchronous approach means that the Client:
● Will have limited face-to-face interactions with the VCA consultant.
● Must raise a ticket and select from the available 280+ services or 10+ packages.
● Must carefully and clearly describe their requirement to ensure accurate and timely delivery. The client is encouraged to use tools to record screencasts or share audio recordings to support their requirements.
Key Questions: Regardless of the service tier, our VCA consultants can service all client requirements. The key questions clients must ask themselves are:
● How urgent and or time critical is the requirement? Silver is for those that want a gradual improvement. Platinum and Platinum+ are for those that want rapid improvements in their cybersecurity posture.
● Do they require frequent Zoom or MS Teams face-to-face calls with the VCA consultants. Platinum+ offers the most amount of face-to-face interactions with our VCA consultants whilst Silver offers the least. Clients can also purchase additional Zoom time in within any of the Service Tiers.
280+ Services across 15 Service Domains
Based on our professional experience & market needs, we have reduced the complex world of cyber into 15 simple domains. Each Service Domain has associated services and activities. We can support you in one or more domains.
6 Key Benefits of our Virtual Cyber Assistant Service
Significant Cost Savings
Our VCA Service leads to considerable cost savings. Not hiring full-time staff means no recruiter fees, no contractors, no salaries, no holiday or sick pay.
Highly-skilled practitioners
With our VCA Service, you get access to highly-skilled cybersecurity practitioners with a wealth of cross-industry experience, at a fraction of the cost of hiring them.
Extension of your IT/InfoSec Team
We can either take on the role of being your Infosec team or we can offer support to your existing team. If your resources are stretched or your require an external professional review of your artefacts, our VCA Service is right for you.
Enhanced Cybersecurity Posture
Our VCA Service is perfect for organisations looking to evaluate their existing cybersecurity maturity and establish a healthy posture in risk management, governance, business continuity & Incident Response.
Complete Cybersecurity Assistance
As the name suggests, our Virtual Cyber Assistants will help you with all your cybersecurity requirements including supplier questionnaires, Cyber Essentials, Incident Response Plans, Playbooks and much more.
Unparalleled Flexibility in Service
The USP of our VCA Service is the incredible flexibility it offers. You can choose from 4 Service Tiers (Silver, Gold, Platinum & Platinum+), 280+ Services & flexible payment options to make a choice that's absolutely fit for your business.
Trusted by

.png?width=800&height=362&name=FIFA_series_logo.svg%20(1).png)



.svg.png?width=1200&height=389&name=1200px-Capita_logo_(2019).svg.png)
What's the Best Service Tier for You?
Silver: This tier is for an organisation who has an established internal team that looks after cybersecurity, risk, governance and compliance but needs an external professional 'pair of eyes' and oversight on an ad-hoc basis. Subscribers receive 12 days of consultancy per annum in the Silver Tier.
Gold: This tier is for an organisation whose limited resources are stretched and they are juggling multiple responsibilities. They need a more consistent, structured and professional support in enhancing their cybersecurity posture and maturity. Additionally, this tier incudes licenses and access to our NCSC Assured Training in Cyber Incident Planning & Response and other courses. Furthermore, you can carry forward hours in this tier. (T&Cs apply) Subscribers receive 24 days of consultancy per annum in the Gold Tier.
Platinum and Platinum+: These two tiers are designed for organisations that either do not have any available resources assigned to cybersecurity or require significant hands-on assistance in creating and defining controls, processes, policies and procedures. These tiers offer the maximum number of hours and increased flexibility in face-to-face communications, maximum discount for procuring additional hours and access to additional, enhanced cybersecurity services and packages. There are additional course licences available in these tiers.
Platinum+: This is the tier with the most features and benefits. Organisations in this tier can raise emergency requests and have timed access to C-level practitioners. In this tier and subject to availability, our consultants will join scheduled meetings over and above the allocated face-to-face calls. Furthermore, we will endeavour to maintain continuity by assigning the same VCA to your account.

Listen to what our clients have to say about our consultancy services
"In order for BMJ to the right way forward we looked for a VCISO to advise us on the right way to do things and give us expertise. We went to Cyber Management Alliance and it's been about a year now and we ran workshops, looked at our response to incidents, created the incident response plan and we are in a position now where we understand our way forward. Our VCISO keeps us on our toes and overall it's been a very effective way of delivering expertise into the organisation that we wouldn't have normally had."
Aaron Townsend, Service Delivery Manager, British Medical Journal
Service Tiers
Benefits, Features & Pricing
Here is a closer look at what each Service Tier offers
- Annual
- Monthly
- GBP
- USD
- EUR
There are specific terms and conditions for many of the features & benefits listed above which can be explained on a detailed call.
Popular Packages to Get You Started Immediately
ISO 27001 Readiness Package (Readiness - Create and/or Refresh)
We will support the organisation to create and adapt to cybersecurity framework based on ISO 27001. We will evaluate the current posture, provide recommendations for improvement, Create relevant policies and processes. Develop a Risk assessment methodology and assist in conducting Risk assessment. We will also provide you with templates and records to be maintained to ensure alignment to the framework.
Services include:
- Gap Assessment
- Create Cyber Policies
- Create Governance Policies
- Review Cyber Procedures
- Compliance activity trackers
- RA Methodology
- Risk Assessment
- Effectiveness Measurement
- Risk Monitoring/Review of Risk Treatment Plan
- Audit Report Response/Corrective Action Plan
- Management Review Meeting - Create
Continual improvement plans
ISO 27001 Review Package (Review Packages include Review Only)
We can review and comment on your ISMS framework and maintenance practices. We will review the relevant policies, processes, procedures and records.
Services include:
- Review of Cyber Policies & Processes (Documentation set)
- Review of Cyber Procedures
- Gap Assessment (Request & review of evidences to ensure compliance to policies & processes)
- ISO 27001 maintenance/framework review (Training, Risk monitoring & treatment plans, Management review meeting records, Internal audits, etc.)
Cyber Essentials Readiness Package
We will support the organisation to create and adapt to cybersecurity framework to comply to all Cyber Essentials requirements. We will evaluate the current level of compliance, provide recommendations for improvement, create relevant policies and processes. We will also provide you with templates and records to be maintained to ensure compliance to the requirements.
Services include:
- Gap Assessment/Review of compliance to Cyber Essentials requirements
- Create Cyber Policies & Processes
- Create Governance Policies
- Review Cyber Procedures
- Documentation of Cyber Essentials
- Self-assessment Questionnaire
Cyber Essentials Review Package
We can review and comment on your compliance to Cyber essentials requirements. We will review the relevant policies, processes, procedure, and records.
Services include:
- Gap Assessment/Review of compliance to Cyber Essentials requirements
- Review Cyber Policies & Processes
- Review Cyber Procedures
- Review of documentation & Cyber
Essentials Self-assessment Questionnaire
BC & DR Readiness Package
We will support the organisation to create and adapt to the business continuity framework based on ISO 22301. We will conduct BIA (Business Impact Analysis) to identify critical assets and relevant acceptable unavailability periods, and create relevant policies and processes. We will help the organisation develop a Risk Assessment methodology and assist in conducting Risk Assessment. Based on the outputs of the assessment, we will support in creating Business Continuity plans and Disaster Recovery plans. We will also provide you with templates and records to be maintained to ensure alignment to the framework.
Services include:
- Conduct Business Impact Analysis
- Create Business Continuity Strategy
- Create Business Continuity-related policies and processes
- Risk Management Methodology
- Risk Assessment
- Business Continuity Plans
- Incident Response Plans
- Playbooks
- Disaster Recovery Plans
BC & DR Review Package
We can review and comment on your Business Continuity & Disaster Recovery Plans and maintenance practices. We will review the relevant policies, processes, procedures and records.
Services include:
- Review of Business Impact Analysis
- Review Business Continuity Strategy
- Review Business Continuity-related policies and processes
- Review Risk Methodology & Assessment
- Review Business Continuity Plans
- Review Incident Response Plans
- Review DR Plans
- Review Playbooks
- Review DR testing records
Incident Response Readiness Package
We will support the organisation to create Incident Response plans based on industry-accepted frameworks NIST SP 800-61 and SANS. We will assess the current practices in place and suggest recommendations for improvement. We will create Incident Response-related documents including Policy, roles & responsibilities, Processes, and Incident Response Plans. We'll also create playbooks to support timely and effective cyber incident response.
Services include:
- Create Incident Management Policy
- Create Incident Management-related documents - Roles & responsibilities, communication plans, etc.
- Create Incident Management processes
- Create Incident Response Plan
- Create IR Playbooks
Incident Response Review Package
We can review and comment on your Incident Response Plans and practices against industry-accepted frameworks NIST/SANS. We will review the relevant policies, processes, procedures and records.
Services include:
- Review Incident Management Policy
- Review Incident Management Processes
- Review Incident Response Plans
- Review Playbooks
Complete Risk Management Package
We will support the organisation to create and adapt to the cyber risk management framework based on ISO 31000/NIST SP-800. We will identify critical assets/processes, develop a Risk Assessment methodology and assist in conducting Risk Assessment. We will also provide you with templates and records to be maintained to ensure alignment to the framework.
Services include:
- Create Information Asset Registers
- Risk Assessment Methodology
- Risk Assessment
- Risk Treatment Plan
- Risk Monitoring/Review of Risk Treatment Plan
- Management Review Meeting - Create
Review of Risk Management Practice
We can review and comment on your Risk Management Framework and implementation. We will review the relevant methodology, assessment report and relevant records.
Services include:
- Review of Information Asset Registers
- Review of Risk Assessment Methodology
- Review of Risk Assessment Records
- Review of Risk Treatment Plan & Risk Monitoring Process
End-to-End Supply Chain Cybersecurity Management
We will create, review and evaluate your organisational cybersecurity controls for your supply chain management processes. We'll connect with you to understand the areas/services with supplier involvement, data shared, IT controls implemented and high-level guidelines, if any in accordance with the same.
Services include:
- Review supply chain processes & practices (agreements, data sharing practices, cyber security controls, etc.)
- Identify applicable cyber controls
- Create supply chain standard (as per the identified cyber controls that need to be implemented)
- Create supply chain policy
Review of Supply Chain Processes
We can review and comment on your supply chain management processes and its implementation. We would connect with you to understand the areas/services with supplier involvement, data shared, IT controls implemented and high-level guidelines in accordance to the same. We will review the relevant policy, standard and relevant records.
Services include:
- Review of Supply Chain practices
- Review of Supply Chain policy & standard
- Review of Supplier monitoring records
Asset Management Lifecycle
We will help you create Information Asset registers, classify assets and develop cybersecurity integrated processes to manage your asset lifecycle. We will address all types of assets - Hardware, Non-IT, Software, Paper, Staff/People, Electronic, etc.
Services include:
- Review of Asset handling processes
- Create Information Asset Registers
- Assist in Asset Classification & Criticality
- Asset Management Policy and Standard
Review of Asset Management Lifecycle
We can review and comment on your Asset Management processes, Information Asset registers, Asset Classification and overall Asset Management Lifecycle.
Services include:
- Review Asset handling processes
- Review Information Asset registers
- Review Asset Management policy and standard
What makes our Virtual Cyber Assistant service unique compared to traditional consultancy models?
Single Document Review
No task is too small - you could even request review of a single document or supplier questionnaire.
Ask Our Experts Any Questions - At No Cost!
All our subscribers can ask our experts any questions at no cost to the allocated hours.
Pay-As-You-Go Monthly Subscription model
The World's First Truly Flexible Cyber Consultancy Subscription Service.
Pick-&-Choose From Over 280+ Services
You can ask us to Create, Review & Refresh from over 15 Service Domains.
Scale Up/Scale Down
Total flexibility: Upgrade or downgrade your service at anytime using our self-service portal.
Carry Forward Your Unused Hours!
You have been busy and couldn’t use up all the days in your Service-Tier? No problem. Roll them over to the next contract.
NO Need to Raise a PO For Each Project or Task!
Our Cybersecurity-as-a-Service model negates the need for raising separates POs for separate projects.
Why not book a discovery call to discuss your requirements?
Want more information on what is a Virtual CISO, Virtual CISO Services & Virtual CISO hourly rates? Book a no-obligation discovery call with one of our consultants.
The Virtual Cyber Assistant Process Workflow
-
Client selects the appropriate tier. The available tiers are Silver, Gold, Platinum and Platinum+.
-
Client receives a Phase 1 onboarding form. This allows for a better contextual understanding of the Client's organisation.
-
The Client is entitled to a free cyber health check and will receive another link to a health check form. This health check enables the Client and Cyber Management Alliance to understand the strengths and gaps in the particular organisation. Clients that select the Platinum or Platinum+ tier are also entitled to a Ransomware Readiness Assessment.
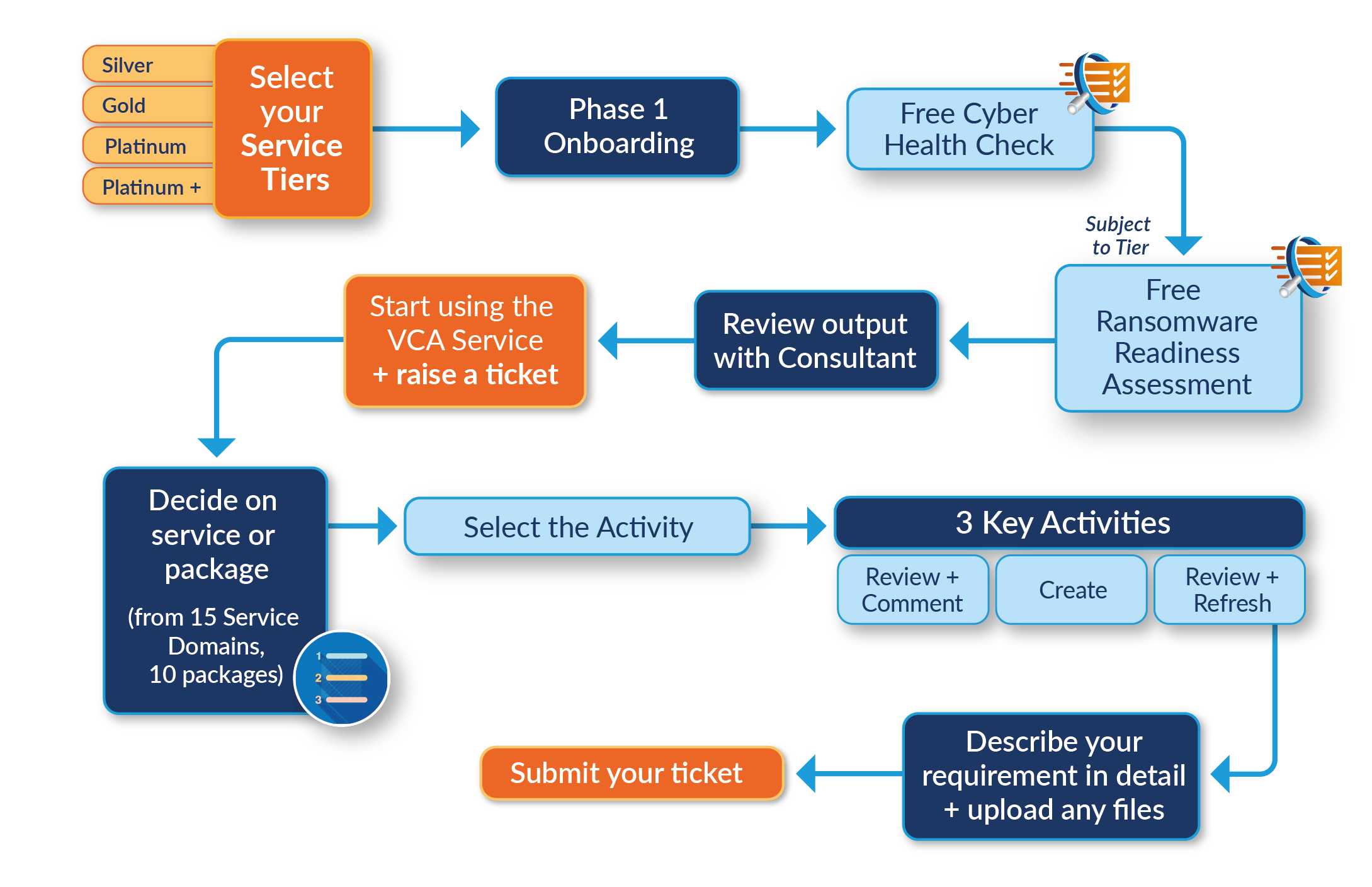
What exactly do you get with our Virtual Cyber Assistant Services?
Here's a quick look at 15 of the main service domains that we cover in our Virtual Cyber Assistant Services UK. There are several sub-categories under each domain, some of which have been listed below.
Cyber Resilience
1. Cybersecurity Strategy
2. Cybersecurity Policy & Procedures
3. Cybersecurity Roles & Responsibilities
4. Crisis Management Procedures
5. Disaster Recovery & Business Continuity Plans
Incident Response
1. Incident Response Plan
2. Policies, Plans & Procedures
3. Playbooks
4. Threat Actor Library
5. Mapping of incidents/Security events
Cyber Risk Advisory
1. Risk assessment
2. Risk mitigation plan/Risk prioritization
3. Audit/Assessment reports
4. Incident tracker & Change management tracker - Major Changes
5. Information asset registers
Supply Chain Cybersecurity
1. Agreements with Suppliers
2. Requirements in Supply chain
3. Evaluation of cybersecurity controls in supply chain
4. Policies & Procedures
5. Evaluation & Monitoring checklists
Certifications & Standards
1. Gap assessment
2. Measurement of effectiveness of controls
3. Previous audit report closures
4. Implementation of controls
5. ISO 27001 & Cyber Essentials
Governance & Compliance
1. Policies & Procedures
2. Measurement of effectiveness
3. Compliance to organisational framework
4. Audit plans & Assessment reports
5. Information security strategy
Technology & Architecture
1. Architecture diagram
2. Comparison of solutions
3. Configuration
4. Monitoring
Data Security
1. Information classification
2. Data flow analysis
3. Information access controls/restrictions
4. Data leakage controls
Security Operations
1. Policies
2. IT Procedures
3. Configuration guidelines
4. Incident/Problem Management
5. Effectiveness of IT Security controls
Asset Management
1. Asset Management
2. Information asset registers
3. Information classification and labelling
4. Asset criticality
5. Asset handling procedures
IT Operations
1. IT Operations Security Policies
2. IT Security Operating Processes
3. Configuration Guidelines
4. Incident Management Processes
Audits & Assessments
1. Audit Report Response
2. Audit Report – Corrective Action Plan
3. Audit Plans
Cloud Security
1. Cloud Security Policies
2. Cloud Security Processes
3. Configuration Guidelines
4. Cloud Security Strategy
5. Review of Cloud Service Agreements
Cyber Strategy
1. Organisational Cyber Security Strategy
2. Management Review Updates
3. Continual Improvement Plans
4. Organisational Risk Profile
Business Continuity & Disaster Recovery
1. Business Continuity/Cyber Resilience Strategy
2. Crisis Management Plans
3. Incident Response Plans
4. Playbooks
5. Business Impact Analysis
The information on this page and related pages and documents is Copyright of Cyber Management Alliance Ltd. The VCA or Virtual Cyber Assistant term, other terms, information, concepts, ideas, workflows, processes, procedures and other content that directly or indirectly supports the VCA Service are Copyright of Cyber
Management Alliance Ltd. Copyright 2022.

