Cyber Security is a Board Issue
Date: 10 July 2016

Within the UK, 90% of large organisations and 74% of small organisations admitted having a security breach in the last year (PwC, 2015). This is a significant rise from 81% and 60% respectively in 2014, which is a strong indication that cyber security has never been so important. This powerful and serious cyber threat is likely to continue rising.
The media has been quick to react, adopting ‘cyber’ as a title that appears in numerous headlines on a daily basis. Embedded in this is the common theme that cyber security professionals are in high demand, with a worrying shortage of trained professionals. This problem is so considerable that organisations, such as the UK Cyber Security Challenge, were born in a bid to encourage those looking to begin or transfer to a career in cyber security.
So, surely if an organisation has a team or department to deal with cyber security issues, it’s down to the effectiveness of that team to maintain the security of a company’s data and its assets? Does cyber security affect the board?
One of the main reasons why this concerns the board can be explained in a single word. Impact. While the cyber security team has responsibility over ensuring security, the consequences of an information security breach extend far beyond a single team. There is a belief that there is no such thing as 100% security, meaning that a breach is a case of ‘if’ and not ‘when’. An examination of different impact types provides a greater understanding of how a breach so easily becomes an issue for the board.
One of the most significant impacts for an organisation to consider following a breach is financial. Depending on the nature of the breach, money may have been stolen. This, however, is just the tip of the iceberg. The real cost comes with responding to an incident.
PwC (2015) reported that the current average cost of a breach for large organisations can range between £1.46m and £3.14m, with smaller organisations paying in the region of £75,000 to £311,000. Incident response covers a number of activities ranging from investigating the breach, right through to preventing further breaches from occurring in a similar manner.
If the Information Commissioner’s Office, known as the ICO, discovers that personal or sensitive data was not adequately protected before the breach, a hefty fine may ensue. Personal and sensitive data falls under the Data Protection Act 1998, meaning that data not afforded suitable protection is treated seriously, with a potential fine of up to £500,000.
A number of other impacts must also be considered, including reputation. Quite often, this can translate into a financial impact over a period of time. When a breach occurs and becomes publicly known, trust and confidence in a brand can be lost instantly, resulting in a loss of business. Forbes and IBM (2014) demonstrate in the following figure how reputational impact can end up being the most damaging for an organisation.
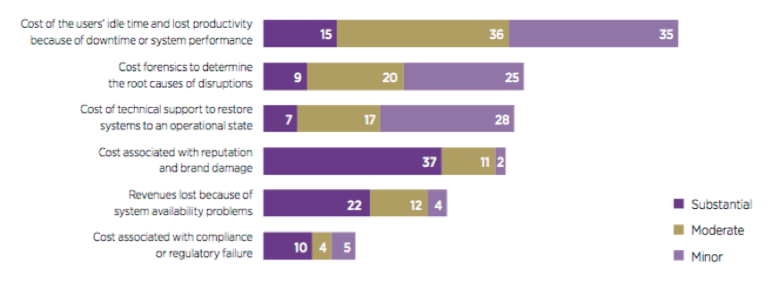 Cost of Cyber breaches
Cost of Cyber breaches
Figure 1: Forbes and IBM (2014) – Impacts of Disruption (survey)
With a damaged reputation, existing customers may choose to leave and at the same time, attracting new customers could prove difficult. Needless to say, when an organisation is the focus of adverse media attention, this inevitably must be dealt with in the boardroom in order to take steps to reduce the impact where possible.
A cyber attack can severely affect a business’ ability to run, resulting in operational impact. If a company is reliant on its IT assets to make money and these are severely disrupted or denied through cyber means, a loss in business can be significant. Operational impact, just like reputational impact, quite often result in a financial impact, too.
These impact types discussed indicate how easily a cyber attack can become a severe and concerning event for an entire organisation, requiring board action to mitigate the effects wherever possible.
A Brief Case Study
Hot off the press in recent weeks has been the recent cyber attack on TalkTalk. The breach resulted in the personal details of up to four million customers being affected, according to Price (2015). Some thefts have occurred following the compromise, with customers discovering money missing from their bank accounts. National scale adverse media headlines have followed the story since it first emerged in mid-October 2015. All in all, the reputational and financial impacts for TalkTalk have been colossal.
The BBC (2015) reported a 14% drop in TalkTalk’s shares following the coverage. Furthermore, MPs are set to launch an inquiry following the breach that exfiltrated the details of such a vast number of customers. Customers are still far from safe, despite arrests. Spin-off crime has resulted, with fake calls to customers managing to successfully glean details that have in turn, led to more stolen money.
Little information has been given about TalkTalk’s efforts to handle the situation, but it is clear from the scale of the hack that this has been a costly and damaging event which is far from over. The results of this breach and its impact clearly extend far beyond the IT department, making it an instant boardroom issue.
So far, the above TalkTalk report has focused entirely on a post-incident viewpoint; the results a cyber attack can have, in order to highlight why board members should consider cyber security very seriously. Pre-incident consideration is also extremely important at the board level, as the right approach from the top downwards can significantly change an organisation’s ‘cyber maturity’ – its defence.
Having an awareness of cyber security at the board level is vital. Courses are available to educate senior executives with crucial knowledge, or alternatively, there is a plethora of free online resources. This can promote better-informed decisions for cyber issues in the boardroom. Some seemingly unrelated decisions in the boardroom could unintentionally create new information security risks. Awareness can help consider cyber security issues when making general business decisions.
Regular communication is key between the board and the cyber security taskforce. With PwC (2015) reporting that 14% of survey respondents had never briefed their board about security risks and 21% not having done so in the past year, defending an organisation can be difficult at best.
Regular monitoring of the threat environment should be conducted by cyber security professionals and passed to the boardroom in a concise form. Spending time considering such information provides a better understanding, which can lead to appropriate decisions being made to support cyber security investments.
One of the areas in which the board should be active is supporting training and education of all personnel, board inclusive. Using the phrase ‘forewarned is forearmed’, even non-technical employees must be given an awareness of the threats. This, in turn, can result in strengthening the human element of the security chain, which is often considered the weakest link.
From a recruitment perspective, the board may wish to provide support, financial or otherwise, to attract and more importantly, retain skilled staff in their cyber security workforce. This can begin with schemes such as sponsoring apprentices or undergraduates in order to facilitate the technical defence needed to protect the organisation, but requires support to enable such schemes to happen.
To conclude, cyber security is for business executives as much as it is for technical folk. Business leaders must be wholeheartedly involved in order to effectively protect their organisations from cyber threats.
About the Author: James is reading an integrated Masters degree in Computer Forensics at the University of South Wales (formerly Glamorgan), due to graduate in 2016. With industry experience in both cyber security and digital forensics, he is extremely passionate about a range of different cyber security issues and disciplines.
Bibliography:
BBC (2015) TalkTalk hack: MPs to hold inquiry into cyber-attack. Available at: http://www.bbc.co.uk/news/business-34635583 (Accessed: 29 October 2015).
Forbes and IBM (2014) The Reputational Impact of IT Risk. Available at: http://www-935.ibm.com/services/multimedia/RLL12363USEN_2014_Forbes_Insights.pdf(Accessed: 29 October 2015).
Price, R. (2015) TalkTalk Hacked: 4 million customers affected. Available at: http://uk.businessinsider.com/talktalk-hacked-credit-card-details-users-2015-10 (Accessed: 29 October 2015).
PwC (2015) 2015 Information Security Breaches Survey. Available at: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/432412/bis-15-302-information_security_breaches_survey_2015-full-report.pdf (Accessed: 29 October 2015).
.webp)



