Cyber Criminals Use “‘Jackpotting’ to Hack US ATMs: Secret Service
Date: 27 April 2018

Cyber criminals are always trying to find different ways to hack devices to make money.
Now they have another way. Called ‘jackpotting’, hacks attacks ATM machines; but to do this, physical access to the dispensing device is needed in order to empty it of all its cash.
Recently, the U.S. Secret Service warned about the effect of ‘jackpotting’.
Two of the world’s largest ATM makers, Diebold Nixdorf Inc. and NCR Corp., have warned that cyber criminals are targeting U.S. cash machines with a tool that forces them to spit out cash in hacking schemes known as jackpotting. NCR said in a recent alert that the first confirmed cases of ‘jackpotting’ losses were in the United States. Diebold Nixdorf and NCR Corp. have said that although these attacks occurred in the U.S., they did not detail whom they have targeted and how much money was deposited .
The attacks were first noticed by a well-known security blog, Krebs on Security, which noted the method was rife in Europe and Asia, mostly in Taiwan and Thailand, but had somehow avoided migration to the U.S. until now. Jackpotting looks like an easy method but in reality, it’s not. However, the payoffs can be large if the method is applied properly. Krebs wrote that it requires hackers to gain access to the ATM machine and deploy a particular malware or specialised electronics solution—often a combination of both—to control the ATM’s operation.
Why is jackpotting working and how attackers are successfully hacking ATM devices
According to Reuters, many of the ATMs in the U.S. are still running Windows XP or other old versions of Windows which are more vulnerable than those running newer operating systems, such as Windows 7. Russian firm, Group IB, says that in 2016 such types of attacks hit more than a dozen European countries, as well as Turkey and Taiwan.
Where did the first attack occur?
The first case of ATM jackpotting wasn’t in U.S. It was first reported in 2013 in Mexico using the malware called Ploutus, which has been identified as one of the most advanced of the ATM malware family in recent years, according to FireEye, Inc.. One of the reasons the attacks took longer to spread to the U.S. is because it may have been easier to get away with physically stealing from ATMs and bribing individuals in Latin America than in the U.S., Hummel said.
“It seems like they’re moving to the U.S. to see how successful they can be here,” he said, adding that the attacks appear to be coordinated and well-orchestrated.
Jackpotting’s journey to America
ATM manufacturers, financial institutions and law enforcement agencies are now scrambling to defend the 400,000 ATMs in the U.S. against further jackpotting attempts—and figure out why it took so long to get here.
So far, jackpotting attacks in the U.S. have largely targeted standalone ATMs—similar to the machines you might see at pharmacies or big box stores. Attacks have already occurred in numerous regions including the Pacific Northwest, New England and the Gulf. "While there is no way to give a definitive answer, there are two predominant schools of thought," says Secret Service Special Agent Matthew Quinn.
"First, financial fraud is cyclical. Attack one region, locally or globally, and move on before apprehension or after law enforcement exposure. The second often revolves around ease of entry. Organised transnational criminal groups may first target a region with less law enforcement presence and less restrictive means of entry."
The U.S. has extensive law enforcement capabilities, making other countries, particularly developing nations, safer training ground for perfecting malicious techniques. But recently, jackpotting has been slowly easing into the U.S. Krebs on Security, who first reported the Secret Service’s advisory, also noted that there were preliminary jackpotting attacks in Wyoming in November.
Man wanted in attempted jackpotting
According to the latest news, three men have been indicted for trying to ‘jackpot’ an ATM in a new crime trend that's hitting the Houston area.
According to Baytown Police, Lt. Steve Dorris said: "The quick action of our patrol officers in responding to this call was key to the apprehension of defendants in this case”.

Juan Carlos Navarro Miranda, 35; Jose Angel Diaz Toledo, 40; and Manuel A. Medina, 37, have been charged with breaching a computer’s security and attempted theft of an ATM. Photo: Harris County District Attorneys Office
They were caught in the act of jackpotting at an Amegy Bank automatic-teller machine on Garth Road. Miranda and Toledo were arrested at the scene wearing fake uniforms in an attempt to pass themselves off as technicians, said Dorris.
According to the report, it's the first jackpotting case in Baytown. Only recently, there been similar attacks on ATMs in the United States, prompting the U.S. Secret Service to warn banks about the scheme.
Do consumers need to worry?
Krebs, the security expert, said consumers don’t need to worry. He told Money that this is not an attack that jeopardises consumer information or funds. Senior technical leader Richard Hummel from cyber security firm FireEye agreed that the average consumer need not be worried.
Hummel said “The biggest issue they would have is an ATM not having any funds available to dispense someone withdraws everything.
Diebold Nixdorf, Inc. and NCR Corp. warned customers that hackers were targeting ATM machines but didn’t identify any potential victims or discuss what the financial losses could be, said Reuters.
According to CNN, a Secret Service memo from mid-January reported at least six attacks have occurred in almost every area of the country recentlyand more attacks have been planned across the U.S.
“The most concerning aspect of the attacks at this point is the level of success the hackers have had accessing ATMs and the possibility of future compromises,” Hummel said.
How it works
Jackpotting is not easy to exploit. It needs patience and physical access to the ATM. According to the Secret Service alert, hackers typically repurpose an endoscope, the medical instrument usually used by doctors, to find the the internal portion of the ATM. Once found, they connect a cord to sync their laptops with the internal computers of the ATM.
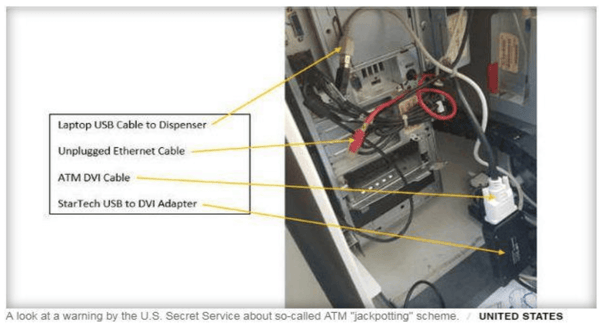
Once connected, the ATM will read out of service’ to customers and the machine can be remotely accessed via SMS, or an externally connected keyboard.
In previous attacks, says the Secret Service alert, “...the ATM continuously dispensed at a rate of 40 bills every 23 seconds,” until it is emptied of cash, or someone on site manually stops it by pressing cancel on the keypad.
So-called ‘money mules’ carry out the attack and collect the money, which can happen within minutes.
The Secret Service recommends that ATM operators update their ATM software from Windows XP to Windows 7, or another updated operating system version to prevent this type of attack.
Reference : https://krebsonsecurity.com/2018/01/first-jackpotting-attacks-hit-u-s-atms/
Reference : http://time.com/money/5125106/what-is-atm-jackpotting/
Reference : http://www.chron.com/houston/article/Three-men-indicted-for-jackpotting-ATM-12541247.php
Reference : http://abc13.com/fugitive-wanted-in-attempted-jackpotting-of-atm-in-baytown/3014725/
Reference : https://krebsonsecurity.com/2018/01/drug-charges-tripped-up-suspects-in-first-known-atm-jackpotting-attacks-in-the-us/
.webp)

