Cyber Kill Chain & its relevance in Cyber Incident Response Plans
Date: 30 April 2020
Most online cybersecurity training programmes appear to skip over the important topic of Cyber Kill Chain.
Your cyber incident response training isn’t quite complete if it doesn’t teach you all about the Cyber Kill Chain and how to work with it in case of a cyber-crime targetting your organisation.
This beckons the question – What exactly is the Cyber Kill Chain (copyright Lockheed Martin) and why is it relevant to cyber incident response?
A little background and etymology are befitting here. The term ‘Kill Chain’ actually originates from Military parlance where it is used to describe the steps that the enemy uses to attack its target. In the world of cybersecurity, Cyber Kill Chain pretty much refers to the same thing – the steps the attacker adopts to infiltrate your system and exfiltrate data.
Understanding the Cyber Kill Chain will help the organisation to better anticipate and combat threats to the system, recognize advanced and innovative malware and destroy persistent attacks. The idea that a single defence strategy is enough to keep the bad guys out is antediluvian.
Today, it is imperative to not just have a rock-solid cyber attack response plan in place, but it is also critical to think like the attackers and understand how they operate as a strategy for defending against them. By knowing each and every stage of the attack process, the IT security team has the potential of mitigating an attack at each of those stages.
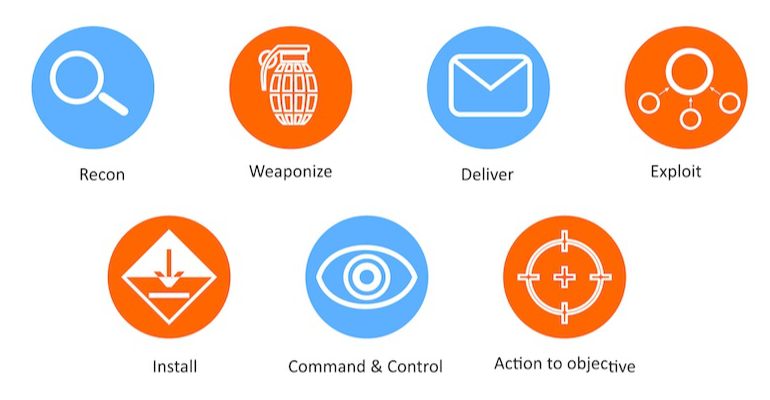
We cover the Cyber Kill Chain in more detail in our NCSC-Certified Cyber Incident Planning & Response Course. But for now, here’s a quick look at the seven steps of the Cyber Kill Chain as developed by Lockheed Martin:
- Reconnaissance: In this step, the attacker gathers all the relevant information about the target. As attackers start trying to gather intel, an aware and well-trained workforce will immediately know that they are under the radar and they can alert their security teams to act accordingly. The employees themselves can be told to act more cautiously at every step putting a big dent in the attacker’s plan.
- Weaponization: Here the attacker prepares the attack tool in the form of an infected document, for example, or a malware. In this stage, there is little than an organisation can do to mitigate impact.
- Delivery: As the name suggests, this step deals with taking the attack tool to the target. This may be done in the form of a phishing email or via a USB drive that contains the malware. This step can definitely be combatted by an aware and well-trained employee base as they are the ones who hold the power to either enable or disable the delivery of the attack vector.
- Exploitation: In this stage, the attacker actually exploits the vulnerability through which they have attained delivery. Here again, if the target system is updated, has a strong anti-virus protection installed, is carefully monitored and secure, the attack can be combatted to a large extent.

- Installation: Now is when the attacker actually installs the malware on the system. A secure system will thwart malware installation attempts. Further, a team that is well-aware of what constitutes abnormal behaviours in the system will also be able to raise and alarm and prevent the installation step in the Kill Chain.
- Command and Control: The attacker now has an in into the system and will try and gain control of it for remote manipulation. The attacker has to reach out to an external Command and Control system for this step to go through and such abnormal outbound activity can be tracked and blocked.
- Actions on Objectives: So, let’s say the attackers have managed to successfully go through with all the first six steps of the Cyber Kill Chain and start executing the actions needed to cause the harm they want to, is it too late to do anything about it now? Not really. A trained and responsive workforce can still swoop in and prevent the attack from spiraling out of control with the right and rapid response strategy steps even at this stage.
As should be clear by now, a good understanding and a solid grasp on the Cyber Kill Chain can help any organisation and its employees raise an alarm at various stages of the attack process. Knowing the Cyber Kill Chain gives you around 7 great points to actually stop the attack and heavily undo the attacker’s work. It must therefore be part of any cyber incident response planning and training process.


.webp)


