Using Metasploit and Nmap to scan for vulnerabilities
Date: 8 September 2020
-1.jpg?width=1170&name=billionphotos-1857579%20(1)-1.jpg)
In this article, we discuss combining Nmap and Metasploit together to perform port scanning and enumerate for vulnerabilities.
There are certain cases where we can’t just go and run noisy scans with Nmap on our target due to various reasons. One of these reasons is doing a black box test for your client with a firewall or IDS in place that would thwart or alert sysadmins about your Nmap scans.
So, combining two of the most effective tools used in the arena of penetration testing becomes more sensible and plausible for us. Let's assume that we have a client machine assigned to us to perform port scanning and report vulnerabilities.
Scanning for open ports on the client machine with Metasploit
- We start by launching Metasploit and using the port scanner module.
msf 5> use auxiliary/scanner/portscan/tcp

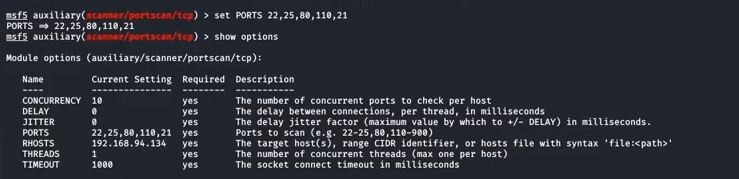
- Next, we set the options for this module with ‘show options’.
- We set the RHOSTS with the IP/IP(s) of our client machine(s) and if we want to customize the scan for specific ports we can do that by changing PORTS.
msf 5 >set PORTS 22,25,80,110,21
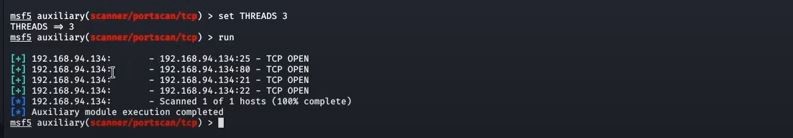
4. After running the scan, we will have an output displaying the open ports on the target client machine we specified earlier.
Combining Nmap with Metasploit for a more detailed and in-depth scan on the client machine
Once we get a clear vision on the open ports, we can start enumerating them to see and find the running services alongside their version.
msf 5> db_nmap -sV -p 80,22,110,25 192.168.94.134
And this is what we get:

Scanning for vulnerabilities with Nmap and Metasploit
Once we are able to find the open ports and the corresponding services running on them, we can carry on our scan to look for detailed version numbers on every service running on each port so that we can then try different auxiliary modules on Metasploit to find possible exploits.
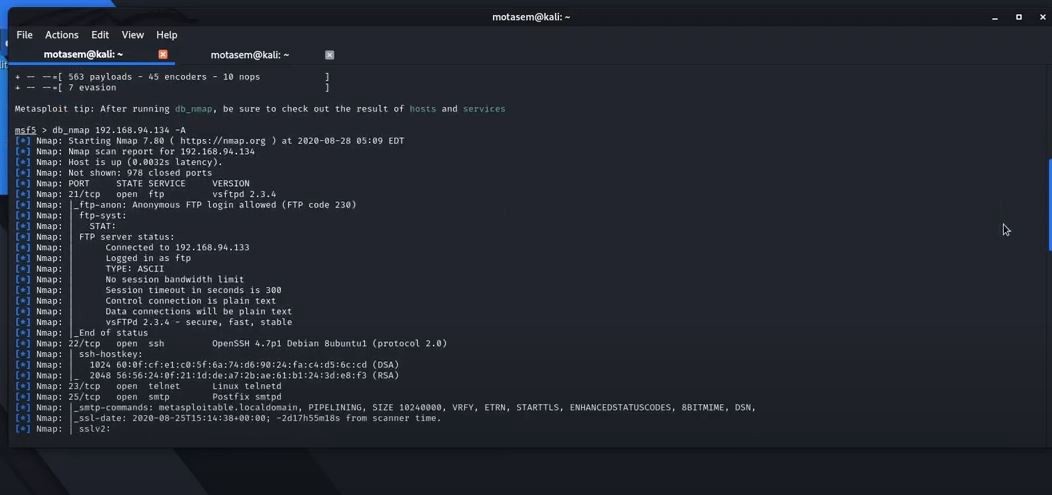
msf 5> db_nmap -sV -A -p 80,22,110,25 192.168.94.134
We'll get the following:
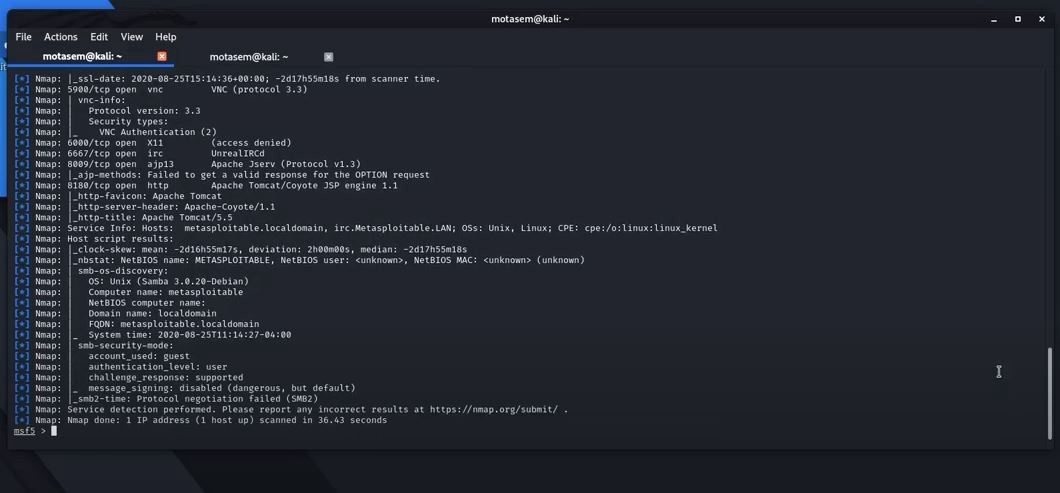
Our next step would be to use Searchsploit to find exploits for the services’ versions we have discovered, or we can use the auxiliary modules built-in Metasploit.
Here is a complete video walk-through.

Motasem is an offensive and defensive cybersecurity trainer and writer. He has an MS in Cybersecurity apart from being a CISSP, E-LPT, Cisco Cyber Ops, IBM Cybersecurity Analyst, Google Cloud Security Engineer.
Read his Research Papers.
You can check out his YouTube Channel.




.webp)

.webp)
