Firewall Facts you must know for the CISSP exam!
Date: 13 July 2020
The Purpose of Firewalls:
- They maintain the routing rules .
- Act as a single choke point (all traffic must pass through the firewall).
- Allow only authorised traffic (accept/ deny rules are applied on both inbound and outbound traffic).
- Enforce immunity against penetration attacks.
Firewall Limitations:
- Ineffective against attacks that bypass the firewalls (e.g. you can access the internet without connecting to the office VPN, thereby bypassing corporate firewall).
- Viruses and malwares could compromise the integrity of the firewall rules and hence the effectiveness of the firewall itself.
Types of Firewalls (More details later):
- Packet Filtering Router firewalls.
- Proxy firewalls.
- Stateful Inspection firewalls.
Types of Firewall Implementations (including placements):
- Single Homed Bastion Host
- Dual Homed Bastion Host
- Demilitarised firewall (also known as Screened Subnet firewall)
Types of Firewalls
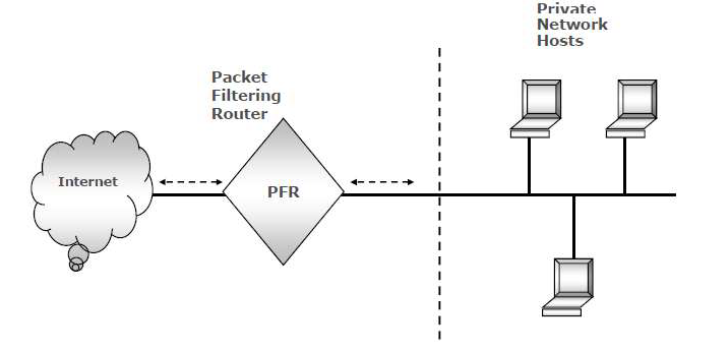
1. Packet Filtering Router (PFR) Firewalls
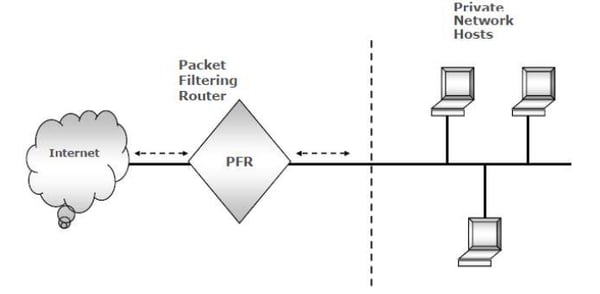
Image source - Shon Harris, 8th edition, CISSP CBK
-
These are also called first-generation firewalls.
-
These apply filtering rules through ACL (Access control lists).
-
As the name suggests, they are implemented via routers and are layer 3 (Network layer) firewalls.
-
They make decisions based on header information.
-
Source and destination IP address
-
Transport protocol (TCP or UDP)
-
Port number
-
PFR could be set to default discard (recommended) or forward (not recommended)
-
Advantage: These are simple to implement, scalable and provide high performance.
-
Disadvantage: Cannot look beyond header information in packets.
- Common Attacks Against PFRs
- IP address spoofing attack (source IP address spoofing)
-
Attacker transmits packets with spoofed IP address so that IP address source (origin) looks legitimate.
-
Countermeasures: Discard outside packets coming in with source IP as internal IP.
-
Source routing attack
- Routers make decisions based on route specified.
- Source routing defines route of IP packets.
- Countermeasure: Drop packets with source routing enabled.
- Tiny fragment miniature attack
-
Attackers expect only first fragment to be examined and the rest are allowed to pass.
-
Countermeasure: Drop packets with tiny fragment configuration enabled.
2. Proxy Firewalls
-
These are also known as second-generation firewalls.
-
As the name suggests, these "proxy" firewalls act as middlemen, intercepting and inspecting messages.
-
Advantages: They break the connection between trusted and untrusted systems, perform screening and re-establish the connection.
-
These can further be classified as two types:
- Application-level gateway proxy Firewalls: Operate at the OSI “application layer” and make decisions on content. These are very slow in operation but extremely secure as they can even look for keywords in the content. These support a wide array of protocols that reside in the Application layer (Telnet, FTP, SMTP, HTTP, SNMP). Application-level firewalls are more popular than circuit-level gateway proxy firewalls.
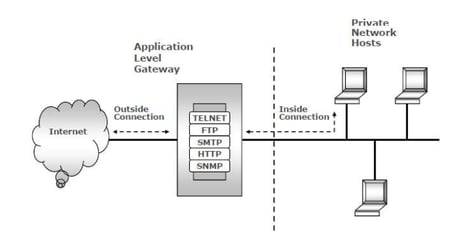
Image source - Shon Harris, 8th edition, CISSP CBK
- Circuit-level gateway proxy Firewalls: They operate at the OSI session layer and make decisions on header information of packets.
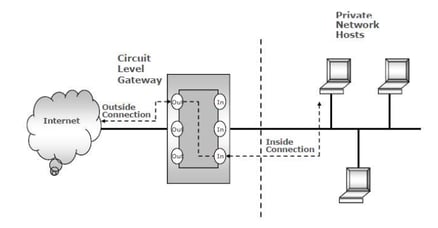
Image source - Shon Harris, 8th edition, CISSP CBK
3. Stateful Inspection Firewalls
-
These are also known as third-generation firewalls.
-
These firewalls keep a track of all connections established and suspended.
-
The details are maintained in a “State table”.
-
Upon receiving a packet, these firewalls look into the state table to check if there is an entry between the source and the destination IP. If yes, this means they have communicated before and hence, more trust is implied. If not, this is assessed as a first time connection.
-
All first time connections will be deeply filtered (firewall will act like an application gateway proxy firewall) and all existing connections would be filtered at basic levels (firewall will act as packet filtering routing firewall).
-
Disadvantage: The state tables are subject to Denial of Service (DoS) attacks.
-
Advantage: These firewalls will balance security and performance (based on entries made in the state table).
See below an example of the state table:
|
Source Address |
Source Port |
Destination Address |
Destination Port |
|
191.168.1.100 |
1030 |
207.7.84.26 |
80 |
|
192.168.1.101 |
1036 |
173.66.31.197 |
80 |
Conclusion
The CISSP exam will not test your knowledge of any vendor-specific firewall technology. But it will test your knowledge of firewall basics, why these are necessary, placement, types of firewalls and the need for them being configured correctly.
The author is a professional CISSP trainer within Cyber Management Alliance’s training pool. He is CM-Alliance’s CISSP/CISA/ISO 27001/SOX/Information Risk Management/SAP Cyber security trainer. He has an MBA (Finance), along with qualifications in Computer Engineering, CISSP, CISA, ITIL (expert), COBIT (foundations), and SAP security.
If you are interested in exploring our CISSP Training & Mentorship programme details and register for your Free CISSP session or contact us at info@cm-alliance.com.
For more information on Cyber Management Alliance, ISO 27001 Certification, our Live Online CISSP Training & Mentorship program, GDPR consultation and workshops, and other courses, webinars, the Wisdom of Crowds live and virtual events, and Insights With Cyber Leaders series of executive interviews, contact us today.





.jpg)

.jpg)
