Threat Intelligence and Cake - The Tenuous Link
Date: 24 July 2018
 Today and beyond, the only certainties are death, taxes and cyber-attacks. The challenge, today and forever ahead, is clear. Wait! One more certainty? Regulations.
Today and beyond, the only certainties are death, taxes and cyber-attacks. The challenge, today and forever ahead, is clear. Wait! One more certainty? Regulations.
How do you build and maintain a cyber-resilient, regulation-ready (think GDPR) business?
A key area of focus must be threat intelligence. Let's cut to the chase:
- If it's not already up there, threat intel (TI) should be put on your must-have-cybersecurity-product list.
- Investing in the wrong threat intelligence feed can be costly and even counter-productive.
- The right kind of threat intel can significantly improve your cybersecurity posture.

I spoke to Tushar Vartak, a leading Middle Eastern bank's CISO on how he sources threat intelligence feeds and how he uses threat intel to stay a step ahead of cyber criminals. It's available here.
Threat intelligence is not well-understood and unsurprisingly, the market takes advantage and flogs painted paper as gold wafers. In this blog, I unravel some mysteries of TI and cover the below key topics.
- Explain threat intelligence to anyone!
- The basics of threat intel
- The Threat Intelligence Value Pyramid
- Applying Threat Intelligence
- Sourcing and key considerations
- Key Takeaways
- Useful links & more information
Who should read this?
- Management such as CIO, CISO, CRO, IT Directors and anyone in charge of reducing an organisation's cyber risk.
- If you are a CISSP, studying for the CISSP, CISM, CISA or if you are an IT or security engineer.
- Auditors and folks in the governance, risk and compliance domains will find this information insightful.
Threat Intelligence and the Poisoned Cake
During our popular cybersecurity training, GCHQ-Certified CIPR course, I explain the threat intelligence value proposition with the following story:
The Poisoned Cake:
 Imagine this: There are ten banks in a country and the CEOs of eight of them have mysteriously died in the last six months. The surviving two have approached you for protection as they suspect that someone is possibly murdering these top executives one by one.
Imagine this: There are ten banks in a country and the CEOs of eight of them have mysteriously died in the last six months. The surviving two have approached you for protection as they suspect that someone is possibly murdering these top executives one by one.
There is big money involved (come on, they are bank CEOs, after all) and you decide to take the contract!
Before you accept the contract, what's one of the first things you should do?
- Buy a few drones with HD camera, extra batteries, and fly them over the executives when they are out, watching every move.
- Order an ambush of bodyguards, similar to the Kim Jong-Un's running chaps.

- Figure out how the other CEOs of the eight banks were murdered; the weapon used, the threat actors and more.
From the three available options, I would hope you selected option number 3. It's simply ineffective and impractical to design any protection, response and recovery strategy without having the information and the intelligence on how the adversaries accomplished these daring murders.
It turns out that on every occasion, the attackers poisoned the cake and pastries with an undetectable poison. So, instead of focusing on the bodyguard ambush, you should ensure that someone (not sure who that unfortunate brave volunteer is) tests the pastries and cakes before the remaining CEOs have their bite.
FYI: I have nothing against cakes. As a matter of fact, they are a weakness and that's how I came up with this simple story.
Tushar Vartak, a deeply experienced cybersecurity practitioner, told me how he built his own malware research lab. A must-see video.
The ABC of Threat Intelligence
 The simplest way to explain what is threat intelligence is to understand how and why governments depend on it. In addition to investing in protection and security, governments spend and put significant effort in the following:
The simplest way to explain what is threat intelligence is to understand how and why governments depend on it. In addition to investing in protection and security, governments spend and put significant effort in the following:
- Threat Actors: Knowing your adversaries. Who are they (often more than one entity)?
- Motivation: Yes, different criminals have different motivations and many times multiple motivations. What are the key drivers for attack?
- Attack Strategies: Understand how that adversary attacks, its modus operandi, the choice of weapons (tools and more).
In a nutshell, yes, you should invest in established technology controls but if you want your business to stand a chance of surviving in the digital, always-connected era, you must focus on and invest in threat intelligence.
We cover the above and much more in our UK Government, GCHQ-Certified workshop. In these workshops, we equip the attendees with an actionable blueprint for building a cyber-resilient business. Read more about it here.
Wait! There is more. The Threat Intelligence Value Pyramid. Read on.
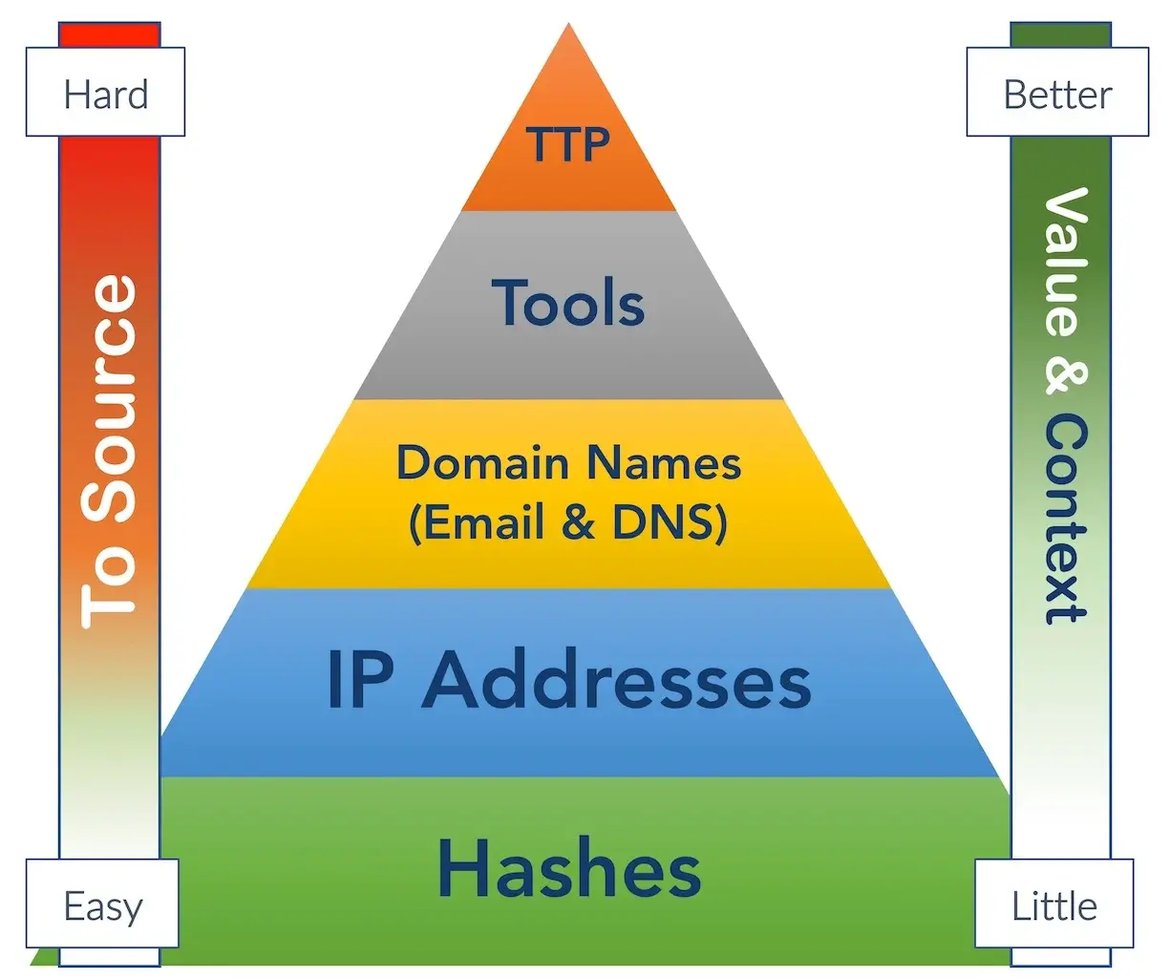
The Threat Intelligence Value Pyramid
An image speaks a thousand words and the below is no exception. The Threat Intelligence Value Pyramid talks of two key things, namely, sourcing and the value. The better, more valuable threat intelligence is more difficult to source. As might be expected, in most cases, the higher up the pyramid, the bigger the budgetary requirements.
I explain each section of the pyramid further down:


Tushar discussed this pyramid and its value proposition in the case study and the video interview.
Simply, a must-see and an essential read.
- Hashes & IP Addresses: Basic threat intel that’s effective in the early stages of the cyber kill chain. Straightforward to produce, easy to obtain and very simple to ingest in most existing technologies like AV or SIEM.
- Often available free of charge.
- Domain Names: Domain names offer better value and protection (caveats do apply) It's sufficient to say here that, to be effective, most bad guys require domain names and DNS to work. Consequently, good threat intel at this level can greatly improve your resilience.
- Available commercially and without cost.
- Tools and Weapons: As we go up the pyramid, it gets harder to produce and obtain quality intelligence. Often, from this layer, the human expert gets involved, putting in time and effort to verify and test before publishing the intelligence. Threat intelligence from here onward can add real value to the cyber resilience posture of an organisation. In many cases, the intel can be ingested automatically but also must be read and understood by other humans so they can plan and design counter actions.
- More often than not, you have to pay for this intelligence.
- TTP: An acronym for Tactics, Techniques and Procedures. Put simply, this type of threat intel offers the best value, is not easy to source and is often the most human-effort intensive to produce. Yes, consequently, it’s also the costliest. However, I repeat, it offers the best value and can truly uplift an organisation's cyber resilience posture.
- In almost all cases (unless procured and supplied by government), this threat intelligence feed is NOT free.
TTP is also used in the attack knowledge-base from MITRE. I will deep-dive into MITRE and the attack methodologies in a different blog. For now, it suffices to say that you should standardise on the MITRE taxonomy.
 Peter Culley, Vodafone's Cyber Intelligence Authority, Tushar Vartak, Director of Security at RAKBANK in the UAE and some crazily-intelligent experts from Kaspersky joined me on a webinar on threat intelligence. Check it out
Peter Culley, Vodafone's Cyber Intelligence Authority, Tushar Vartak, Director of Security at RAKBANK in the UAE and some crazily-intelligent experts from Kaspersky joined me on a webinar on threat intelligence. Check it out
Applying Threat Intelligence in the Business
The WannaCry example is still fresh in most minds, so let's go along with something WannaCry-like. This is a simplification.
Scene 1: Someone stole some deeply-advanced details on weaknesses in ALL Windows systems. (vulnerabilities). The criminal gang who stole this data has successfully auctioned some of these secrets on the dark web.
Scene 2: The other gang, who purchased this exploit, tasked their team members to help them develop this exploit. As part of any good development process one member of the team decides to test the beta version of the malicious file and sends it to an experienced security researcher whom he despises.
Scene 3: The researcher, who works for this security vendor, receives this malicious file. An industry veteran, the researcher, takes all precautions and decides to take a deeper peek into this file from an anonymous email. To his surprise, he observes an entirely new exploit for Windows systems. He is surprised and impressed with the person who created this "weapon".
Scene 4: The security researcher immediately writes a detailed report on this malicious file. In the research he also shares what configurations and updates need to be applied to Windows systems that would render this exploit useless.
Scene 5: The company that hires this security researcher validates this information and immediately pushes it out to its paying customers with clear indication (1) that the exploit is of critical nature and (2) guidance on how to fix the issue and (3) what exact indicators to look out for as signs of compromise.
Scene 6: Within a few hours of distribution of the private threat intelligence report, the criminal gang releases the exploit into the open with two simple objectives - that of causing chaos and earning money. Hundreds and thousands of organisations fall for this never-before-seen exploit except for those who heeded the advice of the security research team.
Sourcing and Considerations
 Referring back to the Threat Intelligence Value Pyramid, I hope it's clear that if you want an effective and mature cybersecurity posture and a cyber-resilient organisation, you must go up the pyramid.
Referring back to the Threat Intelligence Value Pyramid, I hope it's clear that if you want an effective and mature cybersecurity posture and a cyber-resilient organisation, you must go up the pyramid.
Remember, at the top of the pyramid, it's primarily all about human expertise.
Commercial Threat Intelligence Feeds - Key Considerations
- The Human: Ask to meet the human experts that are involved in the threat intelligence production cycle. If possible, ask this expert to give you a summary of current threats.
- Seek evidence: Ask for past analysis and reports. However, as in finance, past performance does not necessarily reflect on the future output.
- Employee Departures: Consequently, ask about any recent employee departures. If there are a few experts who have left (who had a good track record) then it could be a sign of trouble.
- Location does matter: Check to see if the threat intel provider specialises in, or at the least, covers your region. Different regions have different specialist vendors.
- Specialism: During our interview, Tushar touched on the importance of sector specialism as one of the criteria when selecting his threat feed provider. Put another way, if you are in banking, not every threat feed provider specialises in attacks on ATMs.
The Threat Intelligence Journey and Takeaways.
As in all process-based initiatives, cyber resilience is a continuous loop linked to and operating within other business operational cycles. The key thing to keep in mind is this: Protection is important but it is as essential to give equal weightage to making your organisation cyber-resilient and breach-ready.
- To gain maximum value from the upper pyramid you need in-house specialists with the knowledge and passion to digest the context, the TTPs and the situational awareness generated from these private threat intel reports.
- Threat Intelligence comes in many forms. Before paying, do your due diligence and read the section on Commercial Threat Feeds above.
- Remember, depending on your region and the nature of your business, you may NOT receive all the threat intel from a particular vendor, especially when it comes to intelligence from state actors. This is a tiny but crucial point.
- Regulations, yes, like the GDPR, demand that organisations be breach ready. As I discuss and teach in my UK-Government GCHQ certified CIPR course, early detection is a key ingredient of being data-breach ready. Threat intelligence is one very effective way of building effective early detection mechanisms.
Start Your Response Planning Now!
In addition, if you are running a business, of any size, consider getting all the middle to senior management trained on how to plan and prepare for a cyber-attack. All layers of management must have basic security awareness and the knowledge required to make their organisations more cyber resilient.
 Remember, a cyber-attack could easily lead to a data breach, that could put you at odds with the GDPR on several fronts.
Remember, a cyber-attack could easily lead to a data breach, that could put you at odds with the GDPR on several fronts.
To begin planning your incident response, you can download our Cyber Incident Planning & Response mind-map here. We also created an Action Checklist to help you on your journey. You can download the checklist here.


.webp)


