CISSP Concepts– Trusted Computing Base/TCEC, ITSEC and Common Criteria
Date: 28 January 2020

These concepts are from CISSP - Domain -3 Security Engineering.
Trusted Computing Base (TCB) / TCSEC
As the name suggests, TCB establishes the security of a computing device (e.g. a computer). In other words, TCB defines a security profile including hardware, software, inter- process communication and will ensure a computing device will maintain the confidentiality, integrity and availability of the data residing on that system.
TCSEC (Trusted Computer Security Evaluation Criteria) is just another term for TCB.
The term TCB was coined by the US Department of Defence in the Orange book – this book was part of the Rainbow Series of books that defined various computer security standards and guidelines. The Rainbow Series of books was published by the US Department of Defence itself.
Please see table below – that has a list of these security requirements and depending upon the number of requirements, a computing device would comply, a rating (A1 – C1) can be assigned (A1 – highest rating, C1 – lowest rating).
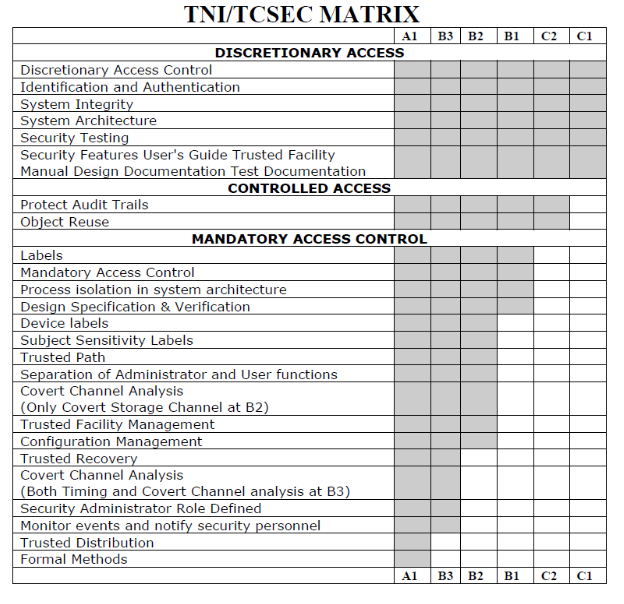
Fig 1 TCSEC rating matrix
Also, worth noting for your CISSP exam is that the TCB framework includes reference monitor, security domain and security kernel – see next
Reference Monitor
This term means (at a theoretical level) that all subject to object access should be controlled. It establishes an access control security policy around a computing device.
Security Kernel
This term means the same as reference monitor with the only difference being that it is the physical implementation (to be remembered) of the access control security policy (Reference Monitor).
Security Domain
This term means establishing the access control security policy by grouping the objects a user can access into a security domain.
IT SEC
This stands for Information Technology – Security Evaluation Criteria. This framework was from the Europeans and was an enhancement to the TCSEC assessment criteria. The ITSEC framework along with the security functions (required security features) also established the security assurance requirements – the level of operating effectiveness of the security function for a duration of time.
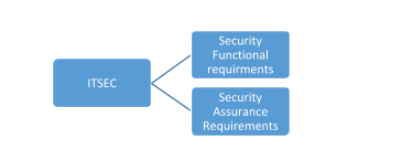
The ITSEC framework also had ratings that were later mapped to TCSEC ratings. For exam, IT SEC ratings are not important to be learned as ITSEC was soon replaced by Common Criteria.
Common Criteria
As the US had TCSEC and the EU had the ITSEC, the rest of the world demanded a universal framework around computing/ technology security evaluation. The Common Criteria information security evaluation framework was adopted as the next and final information security evaluation framework.
Common Criteria allows organisations to specify their security functional requirements and security assurance requirements. This is similar to coming up with a requirement document. In the common criteria framework - this is referred to as Protection Profiles (PPs). Technology suppliers can then implement these requirements and with the support of testing laboratories can get their products (also called “Target of evaluation” in Common Criteria language) evaluated to determine if they really meet these requirements.
Similar to TCSEC and ITSEC, Common Criteria also has a strict rating criteria (please see below). Once this process is completed successfully, a vendor achieves Common Criteria rating for the product.
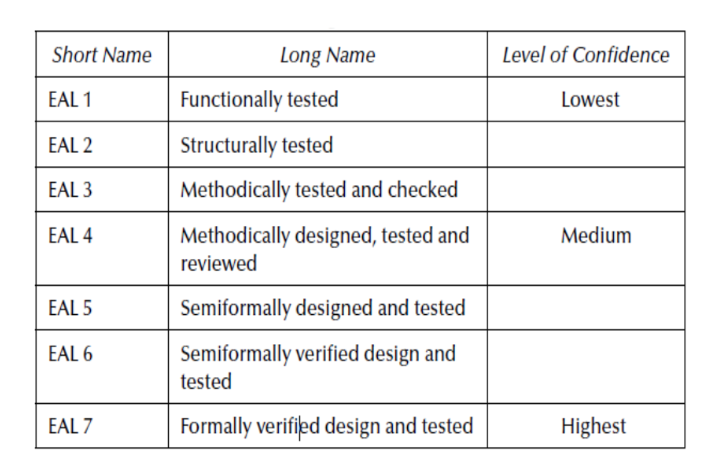
Fig -2 Common Criteria rating matrix
Conclusion
TCSEC, ITSEC and Common Criteria are the three security evaluation frameworks (That one is required to study for CISSP) that define multiple security requirements that a computing device should comply with, and depending upon the number of requirements complied to, a rating is assigned to them. TCSEC was replaced by the ITSEC which was later replaced by the global security evaluation framework - Common Criteria.
The author is a professional CISSP trainer within Cyber Management Alliance’s training pool. He is CM-Alliance’s CISSP/CISA/ISO 27001/SOX/Information Risk Management/SAP Cyber security trainer. He has an MBA (Finance), along with qualifications in Computer Engineering, CISSP, CISA, ITIL (expert), COBIT (foundations), and SAP security.
If you are interested in exploring our CISSP Training & Mentorship programme details and register for your Free CISSP session or contact us at info@cm-alliance.com.
For more information on Cyber Management Alliance, ISO 27001 Certification, our Live Online CISSP Training & Mentorship program, GDPR consultation and workshops, and other courses, webinars, the Wisdom of Crowds live and virtual events, and Insights With Cyber Leaders series of executive interviews contact us today.