Cyber Attack Timelines
Compilation of All Recent Educational Cyber-Attack Timelines for a Historical Perspective on Cyber Crime, Threat Actors & Response Strategies
Cyber Attack Timelines
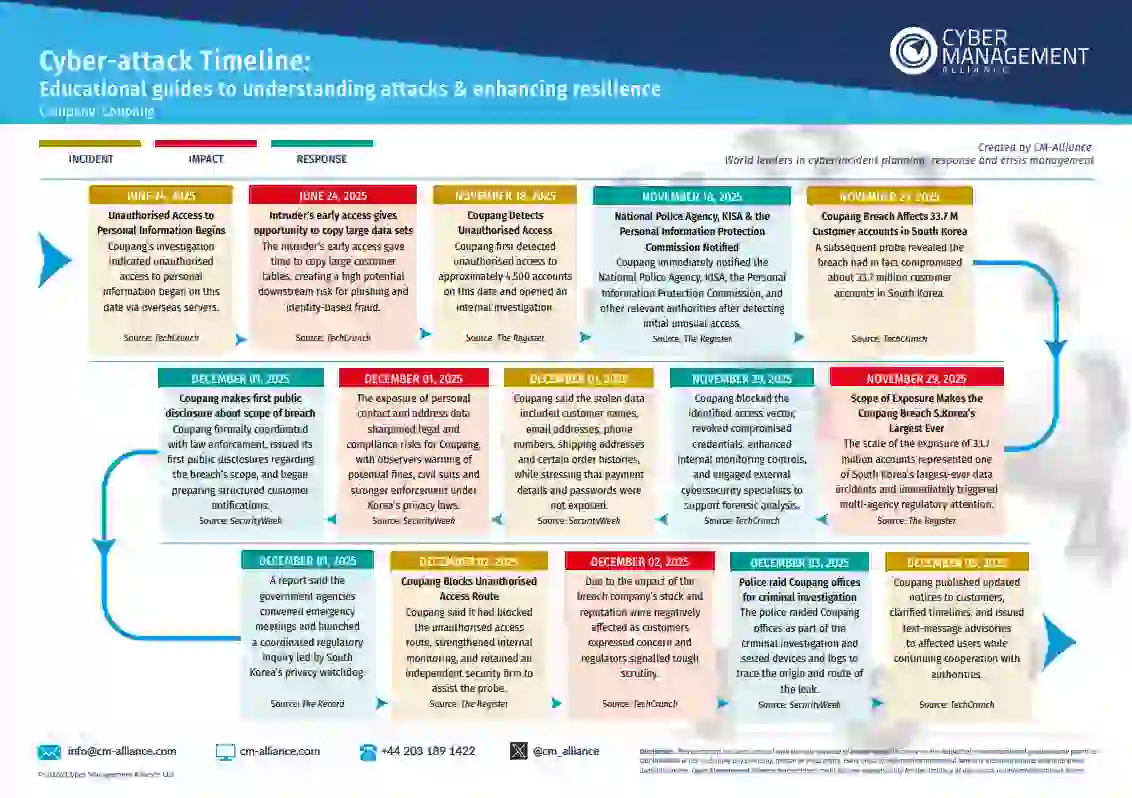
Coupang Data Breach
The Coupang cyber attack was a long-running, stealthy breach rather than a single disruptive event. From late June to mid-November 2025, an unauthorised attacker kept access to Coupang’s internal systems, moved across environments, and reached major customer databases, exposing data for about 33.7 million users.
Our Coupang Cyber Attack Timeline explains how the access started, why it went undetected for months, and what finally triggered containment. Download it for a clear, executive-level view of how insider access, slow credential revocation, and weak monitoring can turn into a national-level crisis. Learn what organisations must fix now to avoid similar failures in the future.
Jaguar Land Rover Cyber Attack
In late August 2025, Jaguar Land Rover faced a significant cyber attack that led to the shutdown of its UK plants and global system outages. The company soon confirmed data was compromised and regulators were alerted. This incident highlights the growing cyber threats impacting not just retail but manufacturing in the UK, where disruptions can cause major financial and reputational damage.
Explore our detailed timeline for insights into the attack's effects—and see how proactive cyber resilience, incident response, playbooks, and regular tabletop exercises can help safeguard your business.

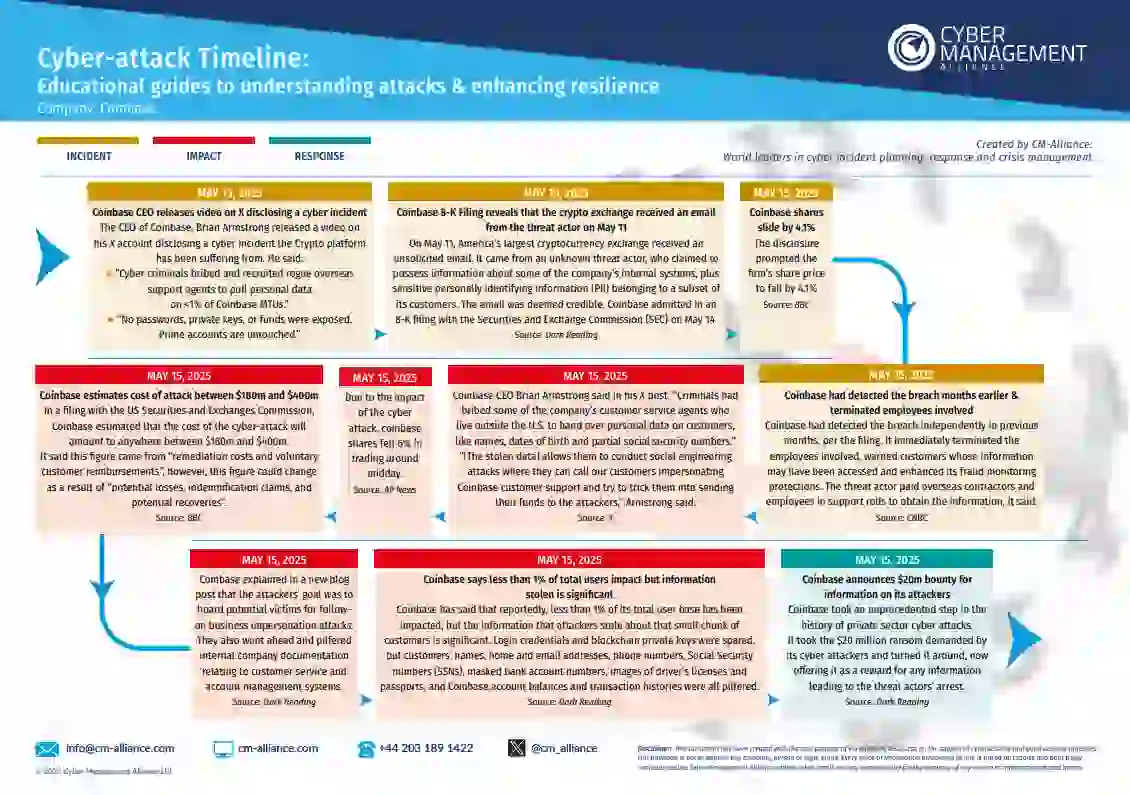
Coinbase Data Breach Timeline
In early 2025, Coinbase uncovered insider collusion involving bribed contractors who stole user data and demanded a $20 million Bitcoin ransom.
The company refused to pay and instead offered a reward for information on the attackers.
Discover key events and leadership decisions in our full Coinbase Cyber Attack Timeline to help improve your incident response.
UK Retail Cyber Attacks Detailed Timeline
In April, major UK retailers including Marks & Spencer, Co-Op, Harrods, and Dior were targeted in a series of damaging cyber attacks.
These attacks disrupted services and exposed sensitive customer data. The attacks were linked to the Scattered Spider ransomware group, marking a significant threat to the UK retail sector.
Explore our exclusive, in-depth timeline for the full breakdown of these shocking events and understand how one of the UK’s most vital sectors came under siege.

.webp)
Marks & Spencer Cyber Attack Timeline
British retail giant Marks & Spencer (M&S) recently made headlines as it fell victim to a sophisticated cyber attack. Its operations were disrupted and online services halted. This inflicted significant financial and reputational damage to the retailer. The breach, attributed to the hacking group Scattered Spider, serves as a stark reminder of the escalating cyber threats facing organisations worldwide.
M&S has reportedly faced losses to the tune of £1billion due to this devastating attack. It has also, apparently, shed over 12 per cent of its value or £1.05billion since the hack on Easter weekend.
We’ve captured everything that took place in this headline-making cybersecurity incident in our Marks & Spencer Cyber Attack Timeline and Visual Summary Image.
Genea Cyber Attack Timeline
Australian IVF provider, Genea, was attacked by the Termite ransomware group with attackers, allegedly, stealing 700 GB of highly sensitive patient and publishing it on the dark web.
The attack caused significant disruption to Genea's operations, with phone lines going down and the MyGenea app becoming inaccessible, leading to patient anxiety and frustration. The breach was detected on February 14, 2025, after suspicious activity was observed on the network, but the impact quickly escalated as patients struggled to contact clinics for urgent medical inquiries and treatment plan updates.
Check out our Genea Cyber Attack Timeline and Visual Summary Image to know all about this major healthcare data breach.
.webp)
DeepSeek Cyber Attack Timeline
DeepSeek, a rising AI platform, was hit by a major cyber attack just as it gained global attention. The incident forced the company to pause new registrations and involved a DDoS attack, malicious infostealer packages on PyPI, and the exposure of two unsecured databases containing over a million sensitive records — including user chats, API keys, and backend data.
Wiz Research discovered the breach, and DeepSeek acted quickly to secure the exposed systems. However, the fallout was significant: Italy banned DeepSeek over privacy concerns, U.S. lawmakers proposed a federal ban, and Texas launched a data privacy investigation.
Explore the full story in our DeepSeek Cyber Attack Timeline and Summary Image.
.webp)
.webp)
Salt Typhoon Cyber Espionage Attack Timeline
The massive Salt Typhoon cyber espionage campaign has been making waves globally, particularly in the US. This supposedly state-sponsored operation has been targeting essential infrastructure, government bodies, and major industries worldwide. Security experts have connected this campaign to advanced persistent threat (APT) groups employing covert techniques to infiltrate and maintain a presence within high-value networks.
We've compiled the developments since these nation-state actors have sought to establish a foothold in critical US infrastructure with our Salt Typhoon Cyber Attack Timeline. Our Detailed Cyber Attack Timeline thoroughly captures these incursions. The Salt Typhoon Cyber Attack Timeline summary visually represents the key events, impacts, and actions taken in this extensive cyber espionage campaign.
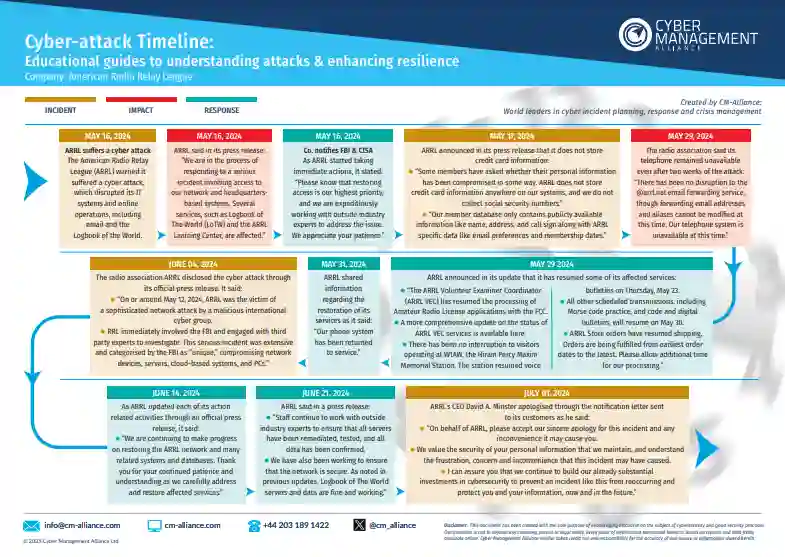
American Radio Relay League Ransomware Attack Timeline
The American Radio Relay League (ARRL), a key organisation in the amateur radio community, suffered a ransomware attack that severely disrupted its operations. Cybercriminals infiltrated ARRL's network, compromising systems and encrypting critical data, including the Logbook of The World (LoTW). The FBI called the attack "unique," citing its advanced nature and widespread impact.
To restore its systems, ARRL paid a $1 million ransom for decryption tools after careful consideration. The organisation prioritised swift recovery while keeping members informed with regular updates on affected services and ongoing restoration efforts.
Discover the full timeline of the ARRL cyber attack in our detailed report and summary image.
%20(1).webp)
Halliburton Cyber Attack Timeline
Halliburton, a leading global Oilfield Services Company, reported that an unauthorised third party had accessed some of its systems. Within a day, it was confirmed that the intrusion was a cyber attack, causing disruptions to Halliburton's operations.
The $23-billion oil drilling and fracking giant reportedly engaged in negotiations with the ransomware attackers while facing significant pressure from its stakeholders. Additionally, the company initiated an investigation with the help of external advisors to evaluate and address the unauthorised activity. Nonetheless, numerous employees reported losing access to essential systems due to the attack.
Find out everything that happened in this attack in our Halliburton Cyber Attack Timeline. Don't forget to read our Halliburton Cyber Attack blog!Evolve Bank Cyber Attack Timeline
Cyber attacks on financial institutions continue to pose a serious threat worldwide, with hackers relentlessly targeting both customer and organizational data.
One high-profile incident that unfolded with unexpected twists involved Evolve Bank & Trust, a prominent U.S.-based banking-as-a-service provider.
The attack, executed by the notorious LockBit ransomware group, resulted in a significant data breach affecting the personal information of approximately 7.6 million individuals.
Check out our Evolve Bank Cyber Attack Timeline where we capture all the twists and turns from this unexpected series of events. Also, don't forget to read our blog on the Evolve Bank Cyber Attack.
.webp)
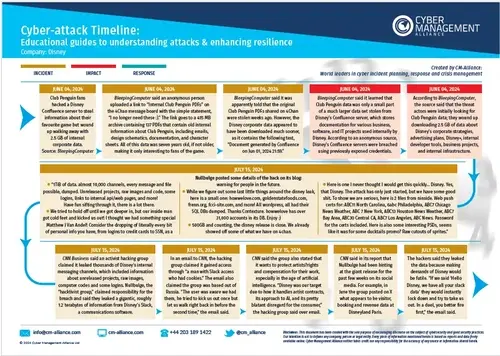
Disney Cyber Attack Timeline
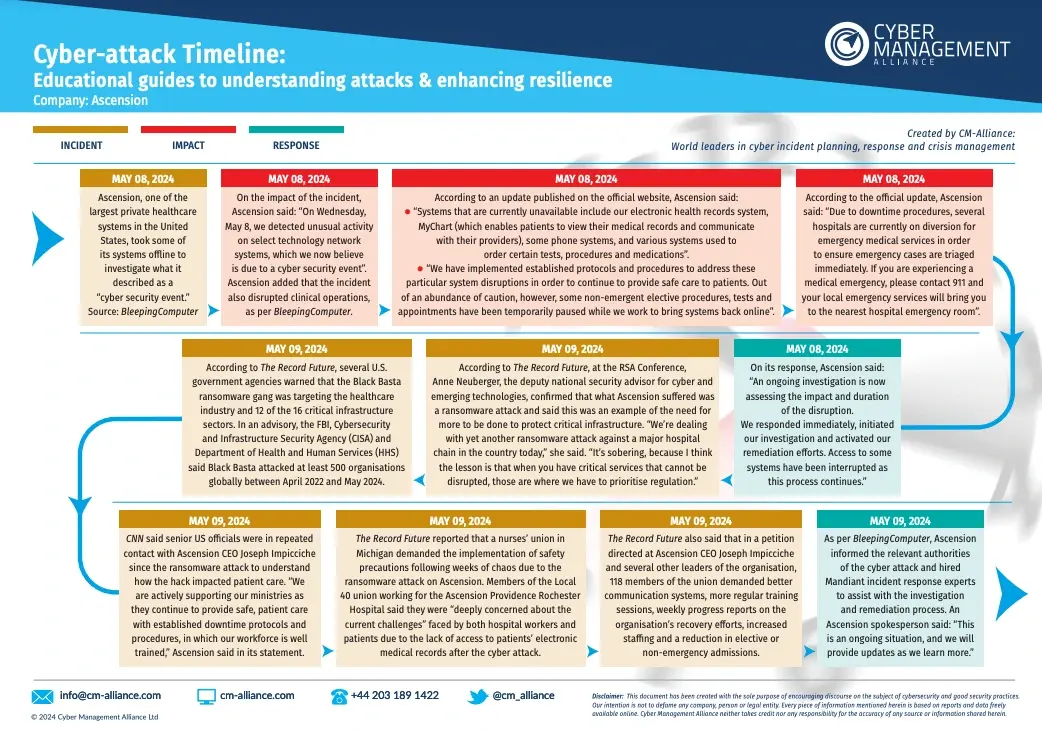
Ascension Ransomware Attack
In May 2024, Ascension Health, one of the largest U.S. healthcare systems, fell victim to a ransomware attack. The breach severely impacted hospital operations across multiple states, disrupting Ascension’s electronic health record (EHR) system MyChart.
Healthcare workers were forced to revert to manual documentation, delaying and disrupting critical patient care.
We’ve uncovered everything that happened in this ruthless cyber assault on yet another major healthcare system in our Ascension Cyber Attack Timeline.

Synnovis & NHS UK Ransomware Attack
Snowflake Data Breach
.webp)

UK MoD Cyber Attack
AT&T Data Breach Timeline
AT&T experienced a massive data breach. Earlier estimates suggested that roughly 73 existing and former customers had their data compromised. The company later confirmed that the actual number was 51 million.
The interesting twist in the tale? One threat actor claimed to have leaked this data back in 2021. Know more about this massive exposure of sensitive information and service disruption in our AT&T Cyber Attack Timeline.

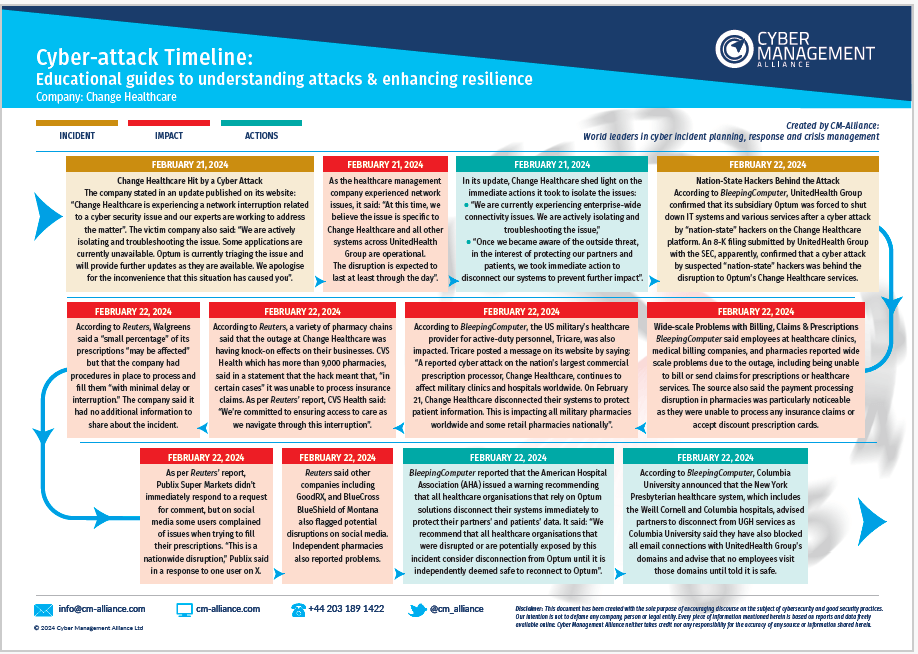
Change Healthcare Ransomware Attack
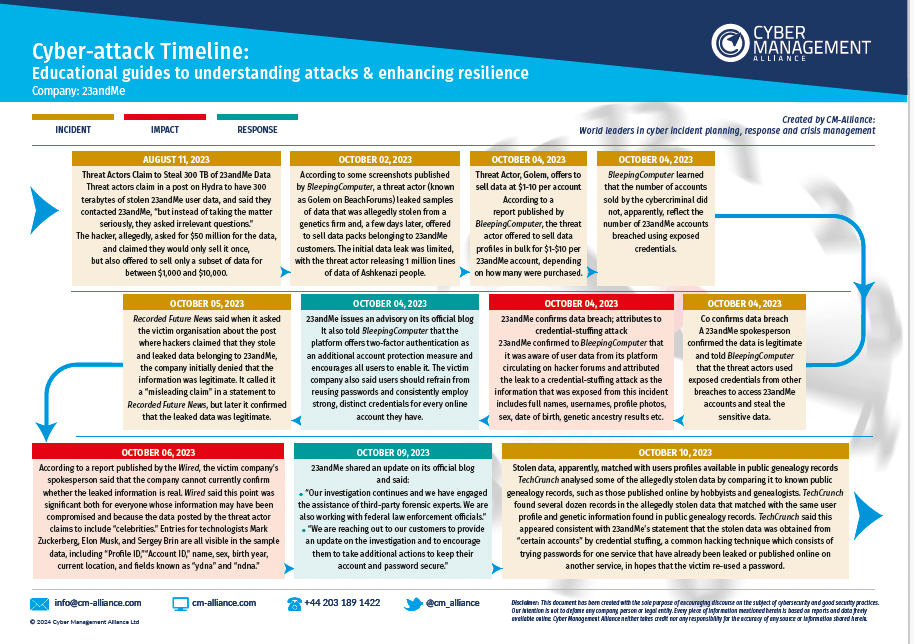
23andMe Cyber Attack Timeline
Our 23andMe Cyber Attack Timeline covers the key events of the attack as it unfolded. The timeline summary image will give you a quick and easily readable overview of what exactly happened and how 23andMe responded. Read these useful documents along with our 23andMe Cyber Attack blog to gain an in-depth perspective of one of the most talked-about cyber attacks in recent months.
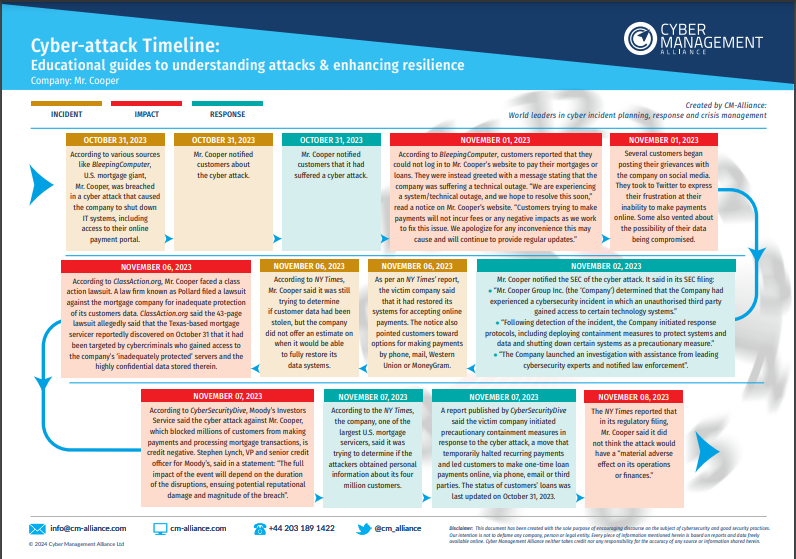
Mr. Cooper Cyber Attack Timeline
Barracuda Email Security Gateway Attack Timeline
Barracuda Networks disclosed a security vulnerability in its Email Security Gateway (ESG) Appliances in May 2023. Although Barracuda promptly issued a patch for this vulnerability and followed up with an additional update, numerous customers had already been impacted. But when Barracuda issued an urgent action notice advising customers with affected hardware to completely remove the vulnerable devices, the cybersecurity community was shook.
Our Visual, Summarised Barracuda Cyber Attack Timeline and detailed document captures exactly how this unprecedented turn of events came about. Read our blog on the Barracuda Email Security Gateway Attack for a quick understanding of what went down in the Barracuda Zero-Day Attacks.

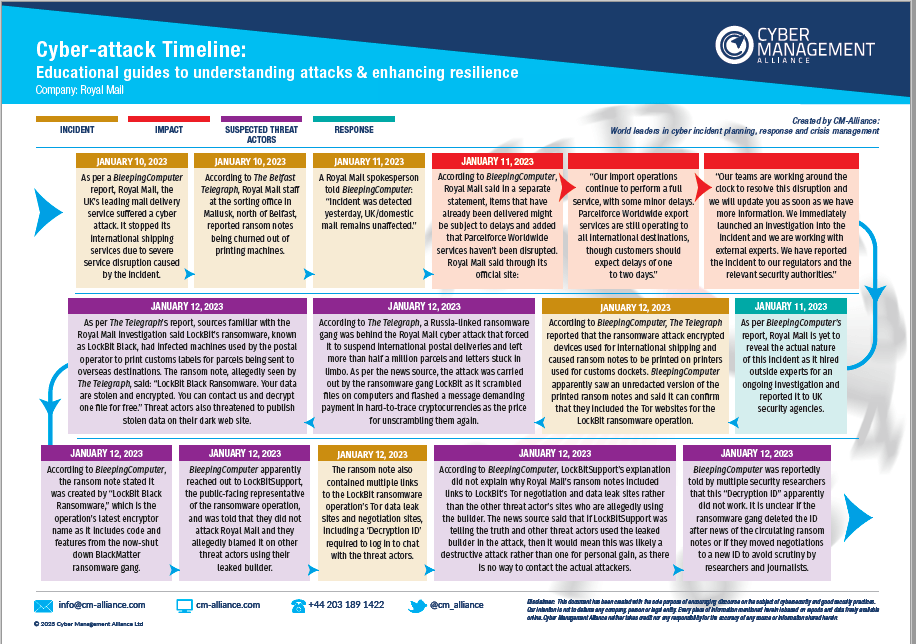
Royal Mail Ransomware Attack
In January 2023, Royal Mail experienced a significant cyber-attack, leading to a halt in its international shipment of parcels and letters via its post office branches. The attack, attributed to the LockBit ransomware group with ties to Russia, involved a substantial ransom demand for a decryption key to restore services.
Check out our educational, visual Royal Mail Ransomware Attack timeline and detailed document on the Royal Mail Ransomware Attack that chronologically details the progression of the cyber incident. This timeline categorizes the information into four distinct sections: the Incident itself, its Impact, the Suspected Threat Actors involved, and the Response to the event. Don't forget to read our blog on the Royal Mail Ransomware Attack.
SolarWinds Cyber-Attack Timeline
Travelex Cyber Attack Timeline
Before being hit by a cyber-attack on December 31, 2019, Travelex was recognized as the world's leading foreign exchange bureau. However, within a mere four months following the attack, this formidable enterprise was put up for sale. Its parent company, Finablr, faced bankruptcy. The deadly combination of a ransomware attack and the subsequent impact of COVID-19 placed the company's 40-year legacy in major jeopardy.
Find out what exactly happened in the Travelex Attack with our Visual, Easy-to-Read Travelex Cyber Attack Timeline and Detailed Timeline Document. Do check out our blog on the Travelex Cyber Attack Timeline for a quick overview of the attack.
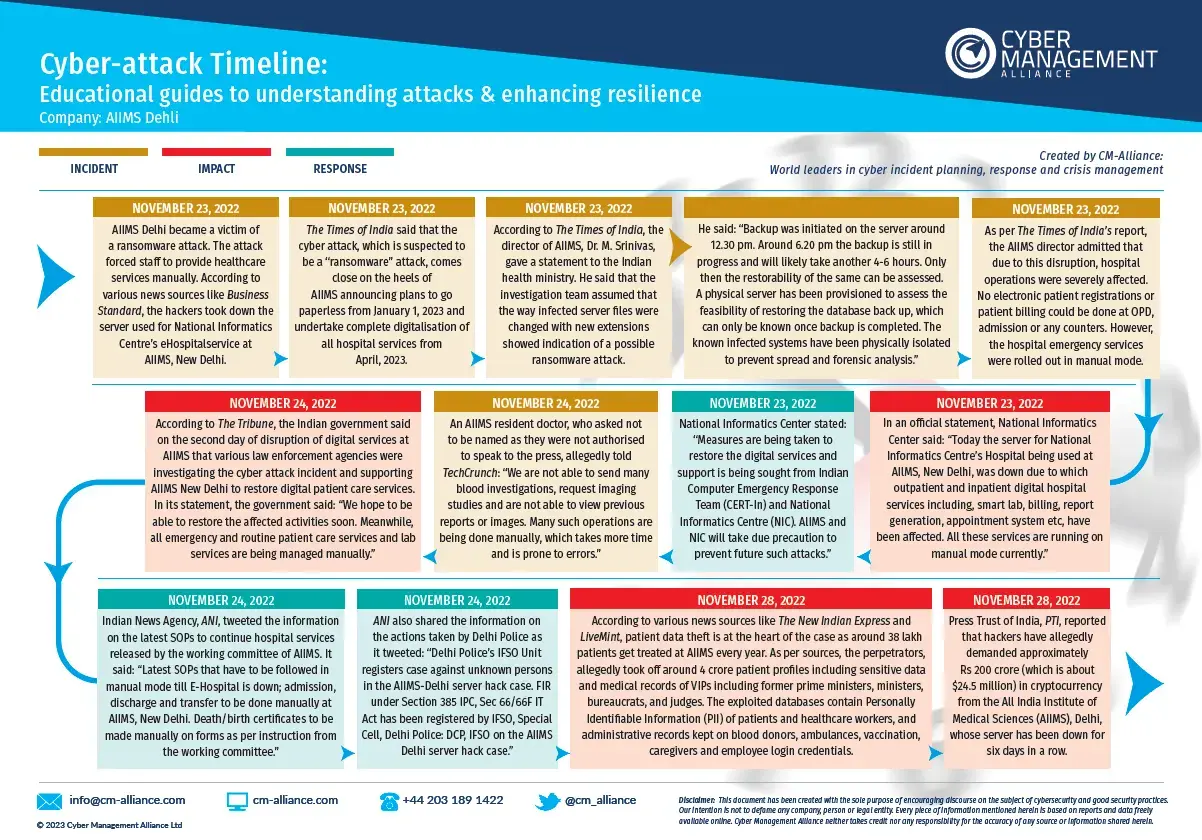
AIIMS Ransomware Attack
The ransomware incident at AIIMS Delhi significantly disrupted healthcare services, deeply affecting a nation where a substantial population relies heavily on public healthcare facilities. This event also amplified the urgency of addressing cybersecurity vulnerabilities in the healthcare sector.
Learn more about how this incident unfolded, what the impact was and how AIIMS and the Indian Government responded to this healthcare emergency. Check out our easy-to-read Visual Timeline, accompanying detailed document here: AIIMS Ransomware Attack Timeline.
You may also want to read our blog on the AIIMS Ransomware Attack.
Western Digital Cyber Attack Timeline
Western Digital, a leading data storage company, suffered a cyber attack in early 2023, during which it was confirmed that hackers exfiltrated 10 terabytes of data, encompassing sensitive customer details. This breach not only disrupted services for users of its My Cloud Home and Sandisk ibi products but also raised alarming concerns due to the attackers' claims of being able to impersonate Western Digital through digitally signed files.
Check out our educational, Visual Timeline on the Western Digital Cyber Attack & the accompanying detailed document. These have been constructed to methodically document the sequence of the cyber incident as it unfolded. You might also be interested in reading our blog on the Western Digital Cyber Attack.
EasyJet Cyber Attack Timeline
Why not book a discovery call to discuss your requirements?
Want more information on the NCSC Assured Training in Cyber Incident Planning and Response? Book a no-obligation discovery call with one of our consultants.
The information on this page and related pages and documents is Copyright of Cyber Management Alliance Ltd. The VCA or Virtual Cyber Assistant term, other terms, information, concepts, ideas, workflows, processes, procedures and other content that directly or indirectly supports the VCA Service are Copyright of Cyber
Management Alliance Ltd. Copyright 2022.
