Western Digital Cyber Attack
Date: 7 September 2023

Data storage giant, Western Digital, was attacked earlier this year and confirmed that hackers stole 10 terabytes of data, including sensitive customer information. Apart from the inconvenience caused to its My Cloud Home & Sandisk ibi customers amongst others, the incident made for terrifying news as hackers claimed to be able to impersonate Western Digital through digitally signed files.
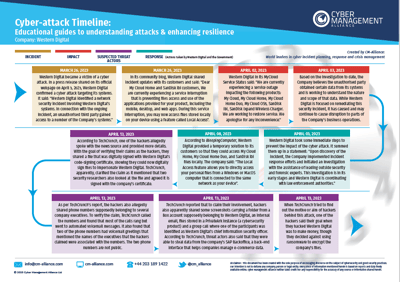
We have created an educational timeline that covers the cyber incident as it unfolded in a chronological order. In this timeline, we’ve categorised the data as: The Incident, Impact, suspected Threat Actors and Response.
The objective behind creating these Cyber Attack Timelines is not to turn the spotlight on the victim but to learn lessons from others' experiences and underline the importance of effective incident response.
Quick reading guide:
Disclaimer: This document has been created with the sole purpose of encouraging discourse on the subject of cybersecurity and good security practices. Our intention is not to defame any company, person or legal entity. Every piece of information mentioned herein is based on reports and data freely available online. Cyber Management Alliance neither takes credit nor any responsibility for the accuracy of any source or information shared herein.
About the Western Digital Cyber Attack
Western Digital became the victim of a "security incident" in April this year. It shared notifications of service disruptions with its My Cloud, My Cloud Home, My Cloud Home Duo, Sandisk ibi, My Cloud OS5 and Sandisk Ixpand Wireless customers who were unable to access files and applications.
However, it soon became clear that hackers had compromised the organisation's systems far more extensively than first met the eye. Hackers, allegedly, shared a file with Western Digital's code-signing certificate with a media organisation to demonstrate how successfully they had managed to penetrate the network. They also appeared to have access to phone numbers belonging to company executives.
And that's not all - they had also apparently gained access to the company's SAP Backoffice besides sharing screenshots of a folder from a Box account supposedly belonging to Western Digital, an internal email, files stored in a PrivateArk instance (a cybersecurity product) and a group call where one of the participants was identified as Western Digital’s chief information security officer.
Though the hackers allegedly admitted that they had attacked Western Digital with the intention of making money, they later decided not to encrypt the company's files. They did, however, supposedly negotiate with the victim and demand an 8-figure ransom in exchange for not publishing the stolen data.
Western Digital Attack Timeline
At Cyber Management Alliance, we are deeply committed to raising awareness about organisational cyber resilience. The attack timelines that we regularly create are meant to educate our network and readers so that they can evaluate their own cybersecurity posture with a microscopic lens and get help where needed.
Our Virtual Cyber Consultancy services are ideal to plug gaps in your existing posture at a pace and budget that suits your requirements. Some of the many areas in which our Virtual Cyber Assistants can help you include:- Creating new and/or reviewing and refreshing your Cyber Incident Response Plans and Incident Response Playbooks.
- Helping you conduct regular cybersecurity drills in your organisation to improve threat perception and ensure better and more coordinated response to attacks.
- Getting proper ransomware response templates and communication plans in order.
- Achieving compliance with regulatory requirements and cybersecurity standards.
- Embracing cybersecurity best practices and implementing a cybersecurity framework.
- Conducting third-party assessments.
- Ensuring better Risk Management, Disaster Recovery and Business Continuity.
This timeline is based only on information that's available freely on the internet and in media reports. Our objective is to simply present this information in an easy-to-consume visual guide that can help cybersecurity practitioners and business owners to understand what happened and how.
Download our comprehensive Western Digital Cyber Attack Timeline.
Lessons Learned from the Western Digital Hack
While Western Digital customers faced several inconveniences through the course of the attack, the organisation handled the incident fairly impressively given its circumstances.
It immediately notified customers and brought in external incident response experts to manage and control the impact. As soon as there was confirmation that customers' data had been affected, it notified the impacted parties.
The fact that it managed to restore operations, bring its network systems back online and stabilise core operations fairly soon shows that there was a certain degree of existing commitment to cybersecurity best practices and disaster recovery.
The fact of the matter is that nobody is going to be spared the wrath of cyber criminals. Sooner or later, even giants like Western Digital can and will be impacted. The only real prevention is protection and preparation. Prioritising cybersecurity is no longer an option, but a necessity for the modern business to survive and thrive - the point we aim to illustrate through this educational timeline.
Disclaimer: This document has been created with the sole purpose of encouraging discourse on the subject of cybersecurity and good security practices. Our intention is not to defame any company, person or legal entity. Every piece of information mentioned herein is based on reports and data freely available online. Cyber Management Alliance neither takes credit nor any responsibility for the accuracy of any source or information shared herein.